![]()
It has never been easier to create and generate both data and information. Data growth is exponential and if you combine that with the growth of an organisation, it becomes ever so easy to get lost in the data-mess and lose overview and control over your data estate in M365. Together we’ll explore some solutions we have in Microsoft Purview and Defender for Cloud Apps which we can use to create some insights to our tenant, user behaviour, potential risks and what we can make out of these.
Note: The following solutions require E5 licensing or equivalent add-on license
Data Security Posture Management (DSPM)
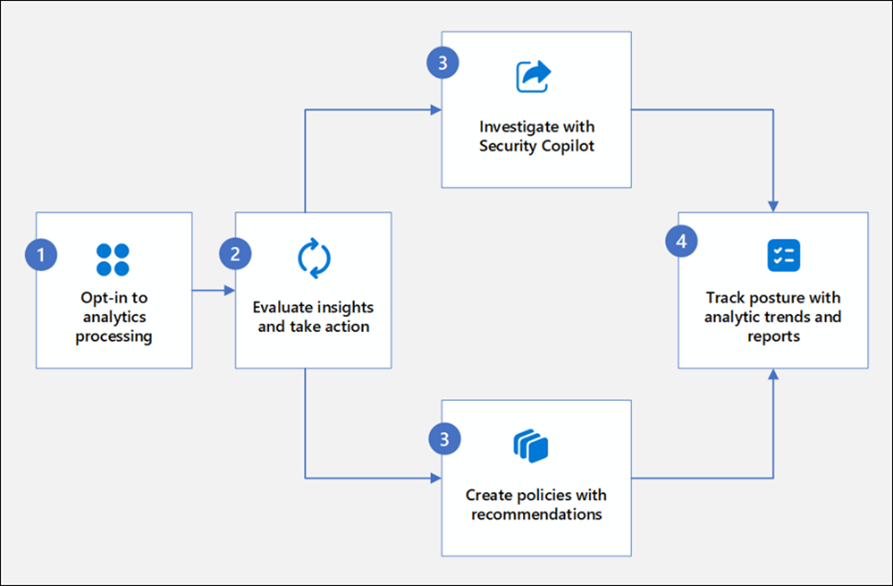
DSPM is a solution that is designed to provide an organisation a holistic overview and visibility into present data security risks and that sensitive data is properly protected in your environments across the tenant and AI.
DSPM automated analytics is quickly configured with a few clicks and after giving it a little time to gather insights it will provide you with insights and recommendations targeting unprotected data such as, but not limited to:
-
- Where sensitive data is located
-
- What sensitive data is unprotected
-
- How is unprotected sensitive data handled, accessed and shared
Data Security Posture Management for AI
Similar to DSPM, DSPM for AI provides insight into how users interact with AI focusing on among other things sensitive interactions and potentially risky interactions.
DSPM for AI will provide you with insights and recommendations such as, but not limited to:
-
- Total interactions over time
-
- Sensitive interactions per AI app
-
- Top unethical AI interactions
-
- Potential risky AI usage
By using DSPM for AI we can get a more general feel for how often users interact with AI during their work, how they use it and analyse reports for potential risks where we e.g. need to implement Data Loss Prevention policies, data security through sensitivity labels and so on.
Insider Risk Management analytics
Insider Risk Management is a compliance solution created to tackle insider risks allowing you to detect, investigate and act on malicious activities in your organisation whether they be intentional or not. While it might take some work to completely implement all the capabilities in production, we can get a lot of value by simply running the Insider Risk Management analytics which does not require setting up any policies.
The analytics will scan M365 Audit logs, Exchange Online, Microsoft Entra ID to identify departing/deleted users (an HR connector can be used here if already set up). The results from the analytics will provide aggregated and anonymized user activities. IRM analytics will provide insights to:
-
- Potential data leak activities
-
- Potential risky AI usage
-
- AI usage trends
-
- Top exfiltration activities
Defender for Cloud Apps – Shadow AI
Microsoft Defender for Cloud Apps allows you as an organisation to gain vital insights to the usage of third-party AI apps. Through Cloud Discovery you gain a list over all discovered AI apps used in the tenant, count of interactions, count of users engaging with the apps, volume of traffic and more valuable information. Each discovered app is assigned a risk score based on several factors, giving you at a quick glance a clear indication of possible threats such as data leakage, compliance violations or simply insecure data handling practices. From this information you can make informed decisions on how to manage or mitigate the surfaced risks.
Need help setting up these solutions or did you uncover some concerning finds? Contact us at contact@infotechtion.com – our team is ready to support you.



