The Infotechtion i-ARM solutions extends Microsoft data risk, security and governance framework, providing a single solution to secure and govern your data estate across M365, Microsoft Azure, AWS, hosted infrastructure and several 3rd party solutions.
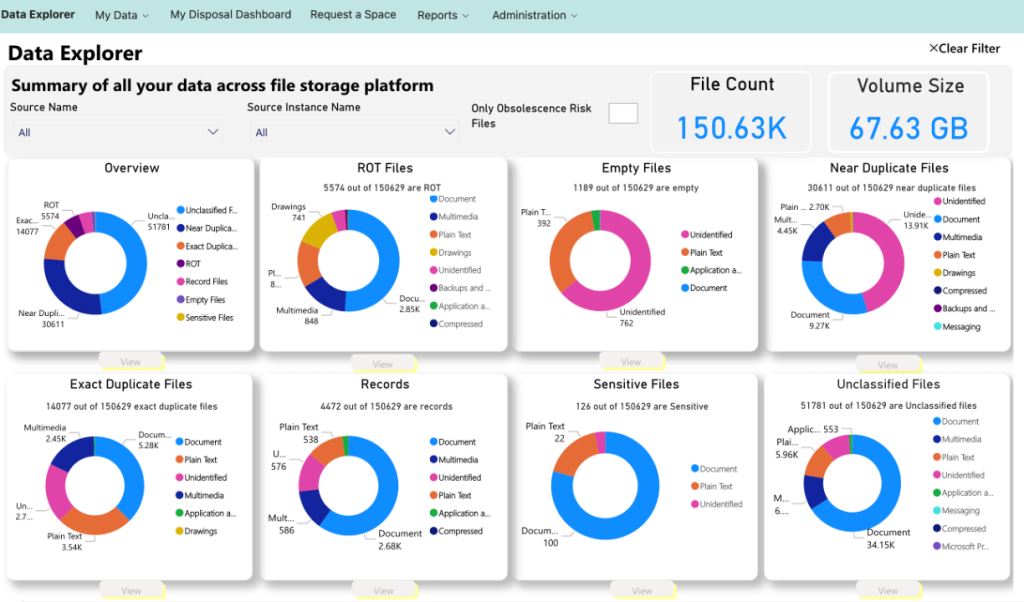
The i-ARM solution leverages the power of AI along with Microsoft Purview to analyze, enrich, and classify information automatically in Microsoft 365, Azure, fileservers, and 3rd party solutions.


Let’s start an amazing project together. We’re excited to hear about your ideas and work with you to turn them into reality. Contact us today to get started.
For any questions

© 2026 ALL RIGHTS RESERVED
Sitemap
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorestandard dummy text ever since.
Please fill the form
Join Infotechtion for an impactful career filled with passion, innovation, and growth. Embrace diversity, collaboration, and continuous learning. Discover your potential with us. Exciting opportunities await!
Please fill the form
By submitting this form you agree that Infotechtion will store your details.
All information provided is stored securely and in line with legal requirements to protect your privacy. You may opt-out any time.