![]()
Microsoft 365 makes collaboration easy. With just a few clicks, users can share files and folders through links, streamlining teamwork across departments, partners, domains and even anyone. But that same convenience opens the door to link oversharing—especially when sensitive information is shared beyond what policy, security, or compliance standards allow.
Link oversharing isn’t about how much is shared—it’s about sharing the wrong things in the wrong way. That includes personal data, confidential business information, or regulated content made accessible through broadly scoped links or folders with inherited permissions.
What Is Link Oversharing?
Link oversharing happens when users share links—intentionally or unintentionally—that provide access to sensitive content beyond its intended audience. It’s a problem not because sharing is bad, but because sharing is done without adequate guardrails for sensitive data.
Typical oversharing scenarios:
- A “Anyone with the link” URL points to a spreadsheet containing customer contact details and personal identifiers.
- A folder shared with an external partner contains a newly added file including medical information or employee health records.
- A daily data extract containing product sales performance containing customer demographic (Full names, location and loyalty card information) is shared with all SharePoint site members, inadvertently including external guests who now have access to potentially sensitive business information.
These are not just productivity missteps, they represent violations of data protection policies, and in many cases, regulatory non-compliance (e.g. under GDPR, HIPAA, or internal information governance standards).
Why Folder Link Sharing Is Especially Risky
Folder-level sharing is particularly dangerous in Microsoft 365 because of permission inheritance. When a user shares a folder: – All existing files become accessible to recipients. – Any new files added later automatically inherit the folder’s sharing scope—even if the content is more sensitive. – Users typically forget to revisit or reassess folder access after the initial share.
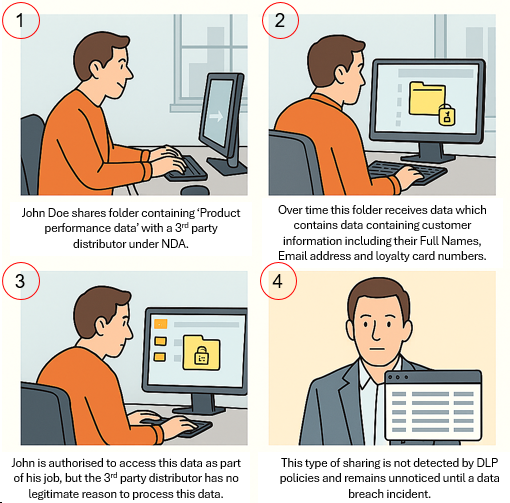
This silent permission creep creates serious data exposure risks, especially when sensitive files are dropped into previously shared folders.
Enforcing Controls through Sensitivity Labels with Encryption
Sensitivity labels in Microsoft Purview allow organizations to classify content and enforce protection policies, including encryption. When used effectively, they:
- Encrypt sensitive files so only authorized users (internal or external) can access them, even if the link is shared broadly.
- Restrict actions like copy, print, or download.
- Apply automatic labelling based on content detection (e.g. presence of medical records or national ID numbers).
- Persist protection even when the file is downloaded or removed from its original location.
This complements link governance by ensuring the content itself carries the protection—not just the container or link.
Educating Users with Microsoft 365 DLP
To prevent link oversharing—especially of sensitive content—Microsoft 365 Data Loss Prevention (DLP) policies can act as guardrails.
How DLP helps:
- Real-time Policy Tips warn users when they attempt to share sensitive content.
- Block or Justify Workflows stop high-risk actions or require business justification.
- Granular Sensitivity-Based Controls adjust sharing rules based on content classification or metadata.
- User Awareness: DLP shifts security left by educating users at the point of risk.
Example:
A user tries to generate a sharing link for a folder containing files labeled “Confidential – Finance.” DLP shows a warning:
> “This folder contains sensitive financial information. Please review the sharing settings or remove sensitive files before proceeding.”
How i-ARM Goes Further
While DLP helps prevent bad decisions in the moment, i-ARM (Intelligent Access Rights Management) ensures long-term governance through automation, risk analysis, and operational remediation of sharing links at Site / File / Folder level.
Key i-ARM Capabilities:
- Discover and score all shared links (especially those tied to sensitive content).
- Flag inherited folder-level permissions that result in overbroad access.
- Revoke or replace unsafe links according to policy.
- Provide ongoing reports and audits of sharing activity.
- Enable remediation campaigns to clean up legacy sharing issues.
- Leverage LLM (Large Language Model) based analysis to distinguish between true and false positives in sensitivity detection.
- Initiate workflows and notifications to allow data owners to review and correct misclassified files, ensuring precision in protection.
Remediating Folder Link Sharing: What You Can Do
Folder sharing can’t always be avoided—but it must be carefully managed. Here are practical strategies to remediate existing risks and improve ongoing governance.
🔄 1. Replace Folder Sharing with Site / File-Level Sharing
- Where possible, share only the specific file(s) required.
- This avoids unintended access to future additions or other unrelated files.
- Microsoft platform has rich auditing of Site and File sharing, but very limited for Folder level tracking.
🦾 2. Enable DLP policies for External and Guest sharing
- Use i-ARM to generate insights of data sensitivity posture across folders.
- Leverage Microsoft Purview DLP to block risky sharing activities.
- Leverage i-ARM to create policies to automatically delete sharing links based on a sharing retention policy.
📄 3. Use Sensitivity Labels on Files
- Even if a folder is broadly shared, sensitivity labels can prevent or restrict sharing of high-risk files inside it.
- Combine with DLP to auto-detect policy violations within folders.
⛔ 4. Block or Restrict Folder Sharing for High-Risk Libraries
- For libraries containing HR, legal, or finance content, configure policies to disallow folder-level sharing altogether.
- Leverage i-ARM to create policies for specific sensitive content categories to automatically detect risky sharing links and remove such links.
🗓 5. Audit and Expire Old Folder Links
- Use i-ARM or Microsoft 365 audit tools to find folders with:
- Broad sharing scopes
- Long-lived links
- No recent access
- Revoke links that are no longer needed or restrict them to named users.
🧠 6. Educate Users About Inherited Permissions
- Many users don’t realize that new files added to a shared folder are also shared.
- Include this in onboarding, security training, and awareness campaigns.
- Leverage i-ARM to generate Site Owner insights related to Data security posture risks.
Best Practices Summary
Action |
Use DLP to warn/block sensitive link sharing |
Deploy i-ARM to discover & remediate links |
Review and remediate folder links containing sensitive files |
Audit and expire links regularly |
Apply sensitivity labels and policies |
Train users on safe sharing behavior |
Benefit |
Prevents oversharing at point of action |
Maintains visibility and control at scale |
Reduces risk of inherited exposure |
Cleans up forgotten access |
Enables automated enforcement |
Reduces reliance on reactive controls |
Learn More
Link-based sharing is highly effective for modern collaboration—but without controls, it becomes a channel for unintentional data exposure. Oversharing is only a problem when sensitive content is shared beyond what policy allows. That’s where DLP and i-ARM work together:
- DLP teaches and enforces preventative controls at the moment of risk.
- i-ARM delivers automated insights of risks, and remediation before / after a DLP intervention.
Get in touch with one of our experts at contact@infotechtion.com to learn more about supporting productive collaboration—without compromising your data security or compliance posture.



