i-ARM AI Governance solution – Secure AI adoption and remediation of existing security, privacy, and compliance risks.
Oversharing sensitive data: AI models may inadvertently expose personal, confidential, or proprietary information in their outputs leading to data breaches, regulatory violations (e.g., GDPR, HIPAA), and reputational damage.
Misinformation & Deepfakes: Generation of false but convincing content, leading to misinformation and erosion of trust.
IP Infringement: Reproduction of copyrighted material or proprietary data, creating legal andfinancial risks
Bias & Discrimination: AI models can amplify biases in training data, resulting in unfair or discriminatory outputs.
Privacy Violations: Outputs may inadvertently disclose sensitive or personal information, violating privacy laws.
Lack of Explainability: Limited transparency in how AI generates outputs reduces trust and hinders accountability.
Over-Reliance: Excessive dependence on AI without human oversight can lead to flawed decisions or ethical lapses.
Regulatory Non-Compliance: Rapid adoption of AI may fail to align with evolving laws and regulations, resulting in fines and disruptions.
Infotechtion’s i-ARM brings the best of corporate information governance from lifecycle management to data protection and security to provide a compliance shield for your AI environment. This protection helps ensure only high quality, current, and risk-free content is made available to Copilot and other AI solutions and therefore to the users of your AI platform.
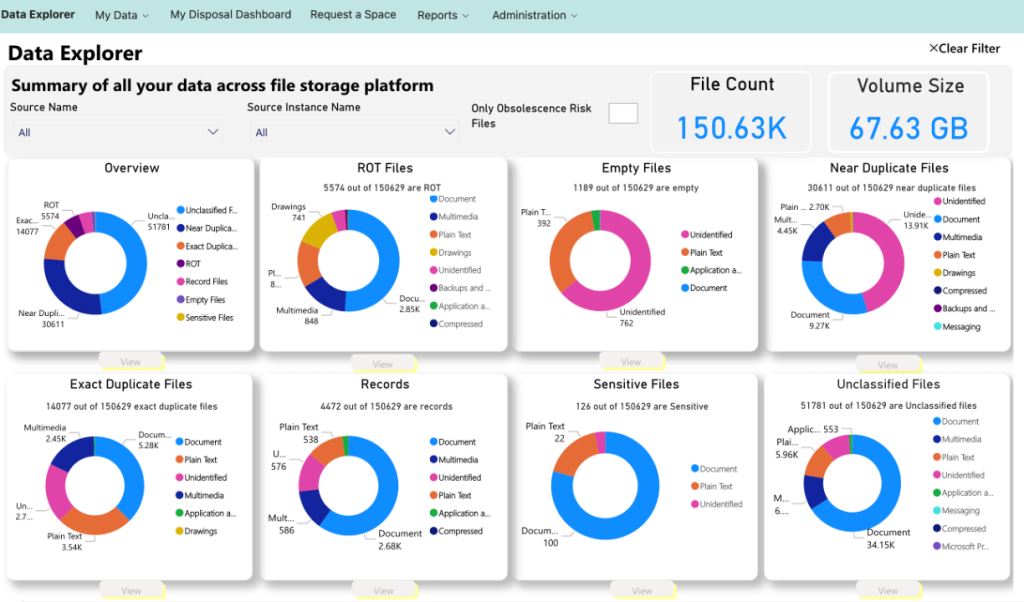
Reduce risk exposure through minimizing captured and reported sensitive data and useless content. Our data explorers leverage captured data in Purview to help identify traditional Redundant, Obsolete and Trivial data (ROT). This keeps this information from accidentally being delivered by AI tools as being valid responses to questions. Similarly, content classified with Sensitive Information Types can be labeled or remediated to minimize risk exposure.
AI progress will be slower than we expect, but faster than we can deal with.
Atle Skjekkeland- CEO of Infotechtion
Let’s start an amazing project together. We’re excited to hear about your ideas and work with you to turn them into reality. Contact us today to get started.
For any questions

© 2026 ALL RIGHTS RESERVED
Sitemap
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorestandard dummy text ever since.
Please fill the form
Join Infotechtion for an impactful career filled with passion, innovation, and growth. Embrace diversity, collaboration, and continuous learning. Discover your potential with us. Exciting opportunities await!
Please fill the form
By submitting this form you agree that Infotechtion will store your details.
All information provided is stored securely and in line with legal requirements to protect your privacy. You may opt-out any time.