Agentic Intelligence (And Why It Matters in 2026)

![]()
Artificial intelligence has reached an inflection point. Models are more capable thanever, benchmarks keep improving, and demos look impressive. Yet many AI systems still fail the moment they encounter real-world complexity. They respond well, but they don’t act. They generate outputs, but they don’t own outcomes. In 2026, the most important question in AI is […]
Surfacing user behaviour and risks in your M365 Data Estate

![]()
It has never been easier to create and generate both data and information. Data growth is exponential and if you combine that with the growth of an organisation, it becomes ever so easy to get lost in the data-mess and lose overview and control over your data estate in M365. Together we’ll explore some solutions […]
The Must-Read Data Security & Governance Series for 2026

![]()
As we head into 2026, AI, Copilot, and rapid data growth are forcing organizations to rethink how data security and governance are designed, operated, and sustained. Microsoft Purview provides a critical foundation—but success in 2026 depends on how you implement, operate, and extend it to support AI-driven ways of working. To help you stay ahead, […]
Navigating Insider Risk Management (IRM): Practical strategies for modern organizations

![]()
In today’s digital landscape, organizations face a complex array of risks—not just from external threats, but from within. Insider Risk Management (IRM) has emerged as a vital discipline for safeguarding sensitive information, intellectual property, and business continuity. But how should organizations approach IRM to balance security, privacy, and trust? Here are practical recommendations for building a robust, privacy-conscious […]
Is Your SharePoint Environment Ready for April 2026?

![]()
April 2026 may feel far away—but for many organizations running SharePoint Online, it’s closer than it looks. Microsoft has announced the retirement of several legacy SharePoint Online records and information management features. When these features are switched off, organizations still relying on them could face compliance gaps, governance disruption, and rushed remediation projects. The key […]
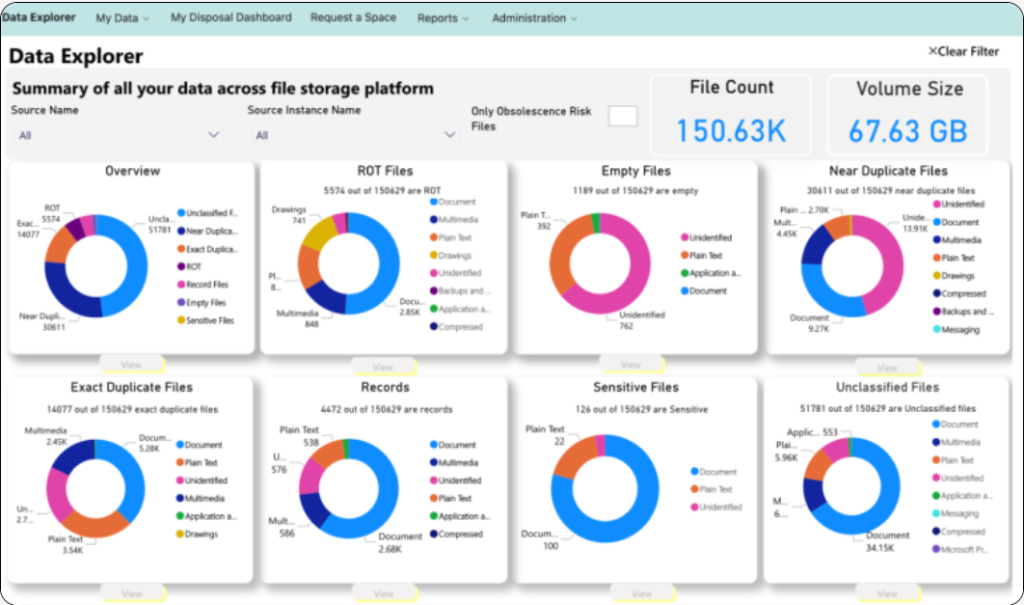
Start with Microsoft Purview. Finish Everywhere with the Infotechtion-ARM.
![]()
Microsoft 365 is now fully embraced by most organizations as the primary platform for collaboration and productivity. Microsoft Purview plays a critical role in securing this environment by protecting information stored in Microsoft 365 and shared from it—using classification, sensitivity labels, encryption, and data loss prevention to control access, external sharing, and usage. For data created, stored, […]
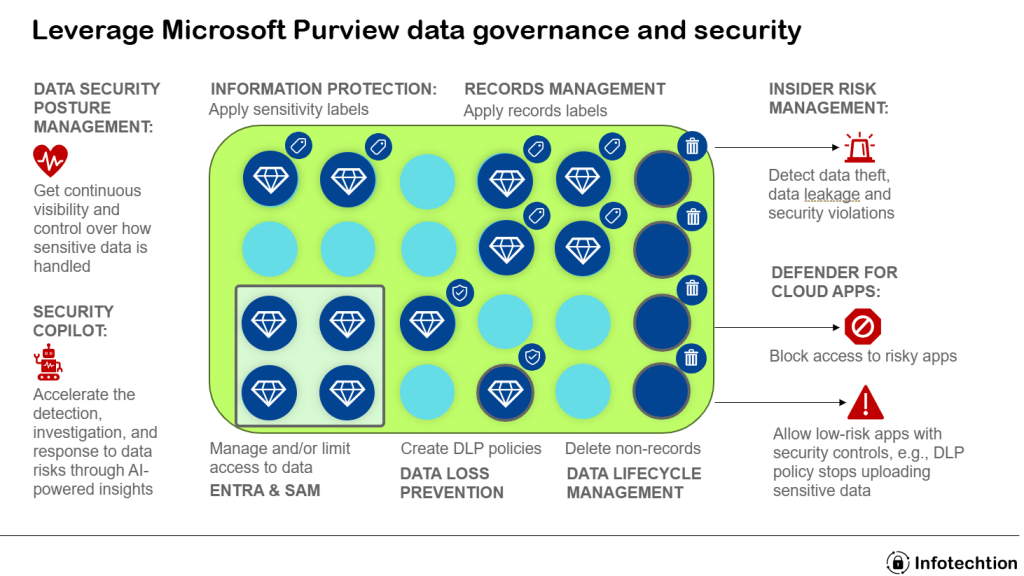
Stop Treating Microsoft Purview Like a Project
![]()
Treating Purview like a one-off implementation—plan, deploy, hand over—produces one-off results. Data grows, risks shift, new controls and regulations appear, and the organization changes. The only way to keep value and risk reduction moving in the right direction is to run Purview as a service, governed by a clear Target Operating Model (TOM). This post […]
Controlled Intelligence: How to Safely Use LLMs in Enterprise Chatbots

![]()
Large Language Models have fundamentally changed what enterprise chatbots can do. They can reason over data, summarize complex information, and interact with internal systems. That capability brings real value, but also a new class of risk that traditional chatbot architectures were never designed to handle. The key mistake organizations make is treating LLMs like deterministic […]
AI and Standards – Preparing for the AI Act

![]()
/*! elementor – v3.21.0 – 26-05-2024 */ .elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px} AI and Standards – Preparing for the AI Act When the majority of the articles of the AI Act take full effect in August 2026, organizations providing, deploying, using or implementing AI systems may need to demonstrate legal compliance depending on […]
Bridging IAM and GRC: Turning Policy Into Action with Microsoft Purview and Entra ID

![]()
Introduction In today’s digital world, identity isn’t just a login — it’s the new security perimeter. Every credential, every permission, and every access request carries potential risk. Identity and Access Management (IAM) decides who gets in, what they can do, and how they’re monitored. Governance, Risk Management, and Compliance (GRC) defines why those controls exist […]

