Trust and interdependency as prerequisites for success during challenging times

![]()
After the second World War, Europe was in ruins and needed to find ways to preserve peace. Part of the solution was to create the European Coal and Steel Community (ECSC), one of the EU’s predecessors. The idea was to create a single common market and to make countries more interdependent on each other. The […]
Protecting what matters

![]()
In today’s digital world, data is everywhere—and so are the risks. From accidental leaks to insider risks and cyberthreats, organizations face growing challenges when it comes to keeping sensitive information secure. Information protection is no longer a “nice to have”—it’s a necessity. According to a 2023 study by IBM, the average cost of a data […]
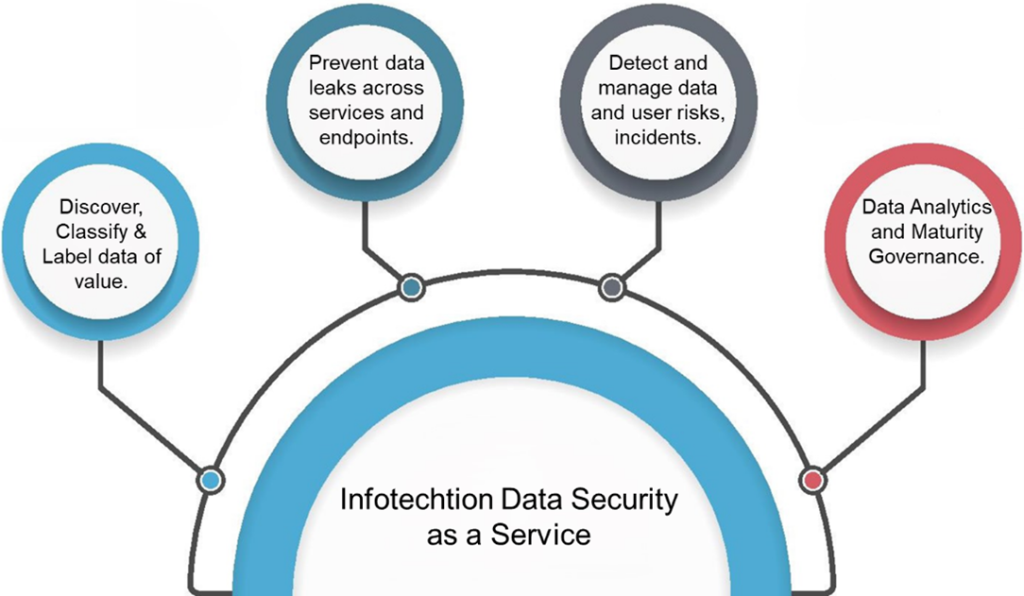
Data Security as a Service: Elevating Your Data Management Strategy
![]()
Unleashing the Power of Comprehensive Data Security In the digital age, organizations face the relentless challenge of managing vast amounts of data while ensuring its integrity, security, and compliance. The adoption of new AI technologies introduces additional complexities, such as the need for robust Data Security frameworks to handle intricate algorithms and large datasets. Infotechtion […]
Configuring Multi-Language Policy Tips in Microsoft Purview DLP: A Comprehensive Guide

![]()
The challenge The ability to deliver Data Loss Prevention (DLP) policy tips in multiple languages, tailored to the user’s selected display language in their Microsoft 365 profile, has long been a priority for many multinational organisations. This capability is achievable through the use of the “NotifyPolicyTipCustomTextTranslations” variable when configuring a rule within a DLP policy. […]
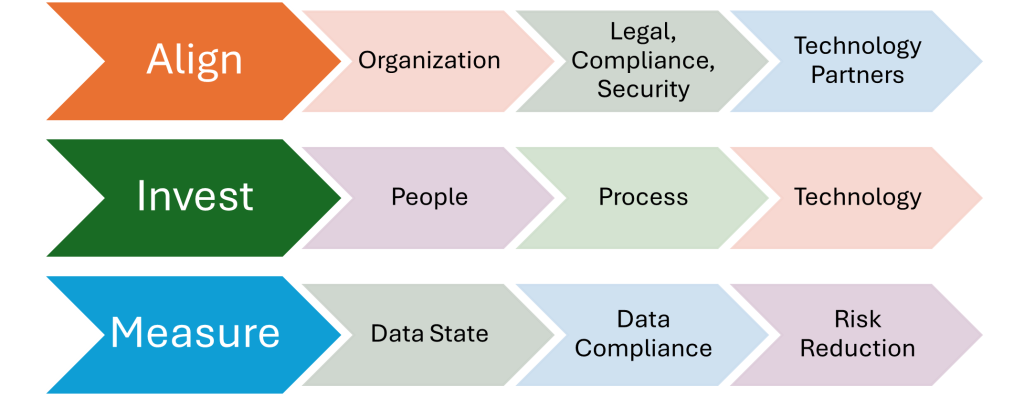
A Guide To Data Governance As A Service Operating Model
![]()
Setting the Foundation for Data Security and Compliance In today’s data-driven world, managing data classifications and lifecycle across enterprise data has become critical for ensuring data security, compliance, and operational efficiency. The Target Operating Model (TOM) offers a comprehensive blueprint to transition data classification activities to a managed service, enabling better process flow, rule enforcement, […]
Securing Data at AI Speed: How Purview Data Security Posture Management (DSPM) Keeps Pace with Rapid AI Advancements

![]()
What is DSPM? Think of DSPM as a security guard for your business’s data—constantly monitoring where your data is stored, who has access to it, and whether it’s properly protected, especially across cloud environments. If sensitive information (such as customer details, financial records, or proprietary business documents) is left exposed or improperly shared, DSPM identifies […]
The importance of a diverse communication strategy

![]()
How does a comprehensive communication strategy lead to successful implementation of changes? As the workforce increases in complexity, so does the need for a diverse communication strategy. Companies must now make meticulous plans to avoid information overload, while also navigate the labyrinth of different demographics, from blue and white-collar workers, remote and in-office workers to […]
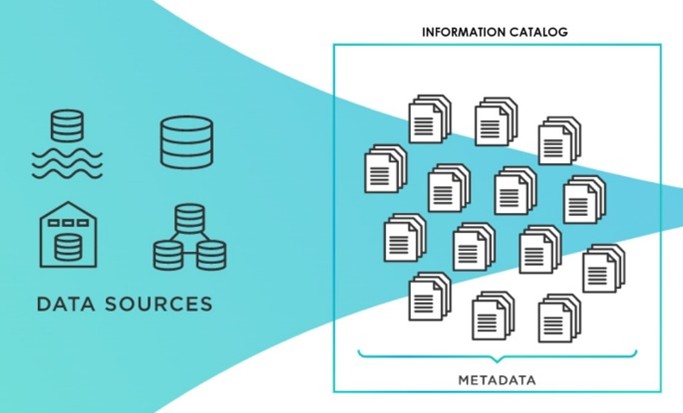
An Information Asset Catalog: Why Now?
![]()
It’s 2025, and most every organization over a few hundred people likely has a Records Retention Schedule. It may have even been extended to include Non-Records, and their related retention and disposition requirements. Most organizations will also have an enterprise architecture management system – a system that stores the applications the organization utilizes. And, more […]
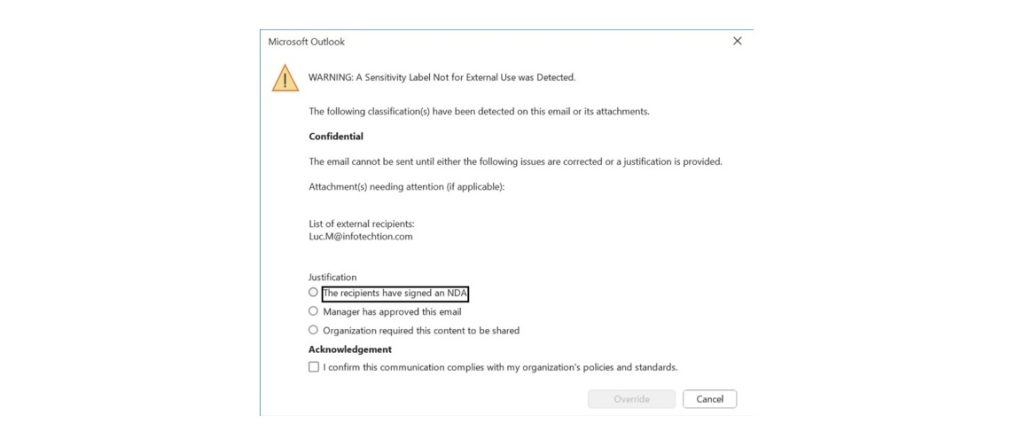
Mastering Purview DLP Email Policies: A Comprehensive Guide to Custom Oversharing Dialog Boxes
![]()
Understanding the challenge When implementing a Data Loss Prevention (DLP) policy in Microsoft Purview, it is essential to adopt a phased approach to ensure its effective deployment. The initial step should involve activating “Simulation Mode,” which facilitates the assessment of potential user impact before the policy is fully enforced. This preliminary stage enables precise adjustments […]
The EU AI Act: Revolutionizing Data Security and Governance

![]()
Artificial intelligence (AI) is transforming industries worldwide, enabling innovation and creating efficiencies at an unprecedented scale. However, with this rapid advancement comes growing concerns around privacy, transparency, accountability, and governance. To address these challenges, the European Union introduced the EU AI Act—a groundbreaking regulatory framework designed to ensure trustworthy and secure AI systems. Central to […]

