![]()
In the evolving digital landscape, cybersecurity has become a critical concern for businesses of all sizes. With over 75% of targeted cyberattacks beginning with an email, the stakes are higher than ever (RoundRobin, 2020). Cybercrime is increasingly used as a tool of political warfare, leading to a surge in attacks on both large and small businesses. As companies adopt new technologies, they not only enhance operations but also expose vulnerabilities that cybercriminals are eager to exploit.
In this context, cybercriminals often perceive small businesses as low-hanging fruit, assuming their security measures are less robust than those of larger enterprises. Financially, these smaller businesses are typically ill-equipped to handle the fallout from an attack, with many lacking even basic cyber insurance and so, for some, a successful breach could prove catastrophic, potentially leading to the end of their operations.
Therefore, it is essential for small businesses to have a robust cyber incident response plan; imagine it as a digital first aid kit ready to handle emergencies, safeguarding your assets and maintaining your reputation.
Common Signs of Attacks on Small Businesses

- Phishing emails – Deceptive emails designed tot rick recipients into divulging sensitive information or downloading malicious software.
- Ransomware & Malware – Malicious software that can encrypt data or disrupt systems, often demanding payment for restoration.
- Weak passwords – Easily guessable or commonly used passwords that increase the risk of unauthorised access.
- Poor patch management – Failure to regularly update software and systems, leaving vulnerabilities that can be exploited by hackers.
Cyber Incident Response Plan – Core Components
Small businesses lacking the fundamentals security measures are ideal targets for cybercriminals and the absence of effective security controls, including comprehensive policies and procedures, combined with the lack of budget for a dedicated cybersecurity team and regular financial transactions make smaller businesses particularly vulnerable. While large-scale security teams may be unrealistic, smaller organizations can still lead in cybersecurity with strategic planning and resource allocation
Here are six core components of an effective Cybersecurity Incident Response Plan:
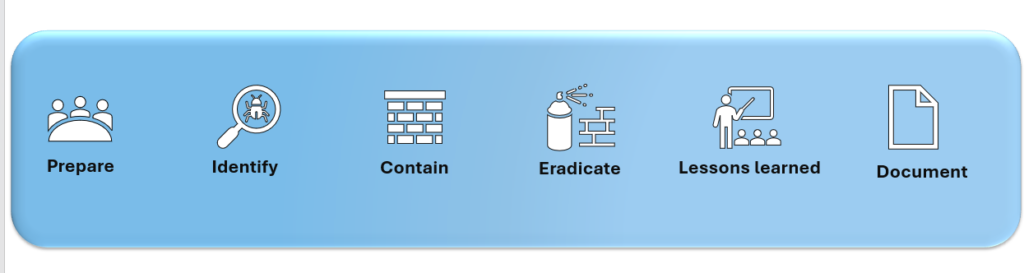
- Prepare
- Assemble a Response Team: Identify key personnel and ensure each member understands their roles and responsibilities during an incident.
- Develop Policies and Procedures: Establish clear guidelines for identifying, reporting, and responding to incidents. Keep these policies updated to address evolving threats.
- Conduct Risk Assessments: Regularly evaluate potential threats and vulnerabilities specific to your business. Prioritize critical assets and define recovery objectives.
2. Identify
- Monitor Systems: Use cost-effective tools to monitor for suspicious activities. Implement Security Information and Event Management (SIEM) systems if budget allows, or utilize built-in monitoring features of your current systems.
- Incident Reporting: Ensure all employees know how to report potential incidents quickly and clearly.
3. Contain
- Immediate Response: Quickly isolate affected systems to prevent the threat from spreading. Implement short-term fixes to mitigate immediate damage.
- Long-term Containment: Develop more permanent solutions to secure your systems against similar threats in the future.
4. Eradicate
- Identify Root Cause: Determine how the incident occurred and eliminate all traces of the threat.
- Remove Threats: Clean systems of malware and any unauthorized access points.
- Restore Systems: Carefully bring systems back online. Recover data from backups and ensure systems are secure.
5. Lessons Learned
- Conduct Post-Incident Review: Analyse the incident response to identify strengths and areas for improvement.
- Update Response Plan: Revise the plan based on lessons learned to enhance future responses.
- Train Staff: Continuously educate team members on new threats and response procedures.
6. Document
- Incident Log: Keep detailed records of the incident, including actions taken and outcomes.
- Secure Storage: Store documentation securely for future reference and compliance purposes.
Importance of Prioritizing Incident Response Plans
Small businesses typically allocate fewer resources to cybersecurity, making a well-crafted incident response plan crucial therefore investing in an effective plan can mean the difference between a swift recovery and a devastating breach.
By following these guidelines and prioritizing cybersecurity, small businesses can better protect themselves against the ever-evolving threat landscape, ensuring resilience and continuity in the face of cyber incidents.
Feel free to contact us at contact@infotechtion.com if you need any help making a well-crafted incident response plan.



