![]()
In today’s digital age, where technology rapidly evolves and integrates into every aspect of business operations, adopting advanced tools has become crucial. One such innovative tool is Copilot, designed to streamline various business processes through intelligent automation and data integration. However, with the adoption of such technology comes the need for robust monitoring and management to ensure security and efficiency.

Understanding the Risks of AI in Copilot Deployment
As organizations increasingly deploy AI-driven tools like Copilot to enhance efficiency and streamline processes, it is crucial to remain vigilant about the inherent risks associated with artificial intelligence. Here are some key considerations for managing these risks effectively:
Data Security and Privacy Concerns
AI tools, including Copilot, rely heavily on data to function optimally. This dependency necessitates robust data governance to prevent unauthorized data access and ensure privacy. The risk of data breaches or inadvertent data exposure is amplified if AI systems are not properly secured, making stringent security protocols essential.
Transparency and Control
AI-driven decisions can sometimes be nontransparent, known commonly as the “black box” issue, where it’s not clear how the AI arrived at a particular decision. Organizations must look for transparency in how AI tools like Copilot operate, ensuring that there are mechanisms in place for human oversight and control. This transparency is crucial not only for trust but also for compliance with regulatory standards that require explainability in automated decisions.
Dependency and Automation Bias
There’s a risk that reliance on AI could lead to automation bias, where users might overlook or undervalue their own judgment, deferring too readily to the AI’s suggestions or actions. This can be particularly risky in critical decision-making processes where human oversight is essential.
By understanding and addressing these risks, organizations can better handle the capabilities of AI like Copilot while mitigating potential negative impacts on their operations and reputations. Implementing comprehensive risk management strategies through tools like i-ARM reporting ensures that the deployment of AI technologies aligns with organizational goals and compliance requirements, safeguarding against unforeseen challenges.
Here, we will delve into the various sections and insights offered by i-ARM reporting to organizations.
Overview of Copilot Report
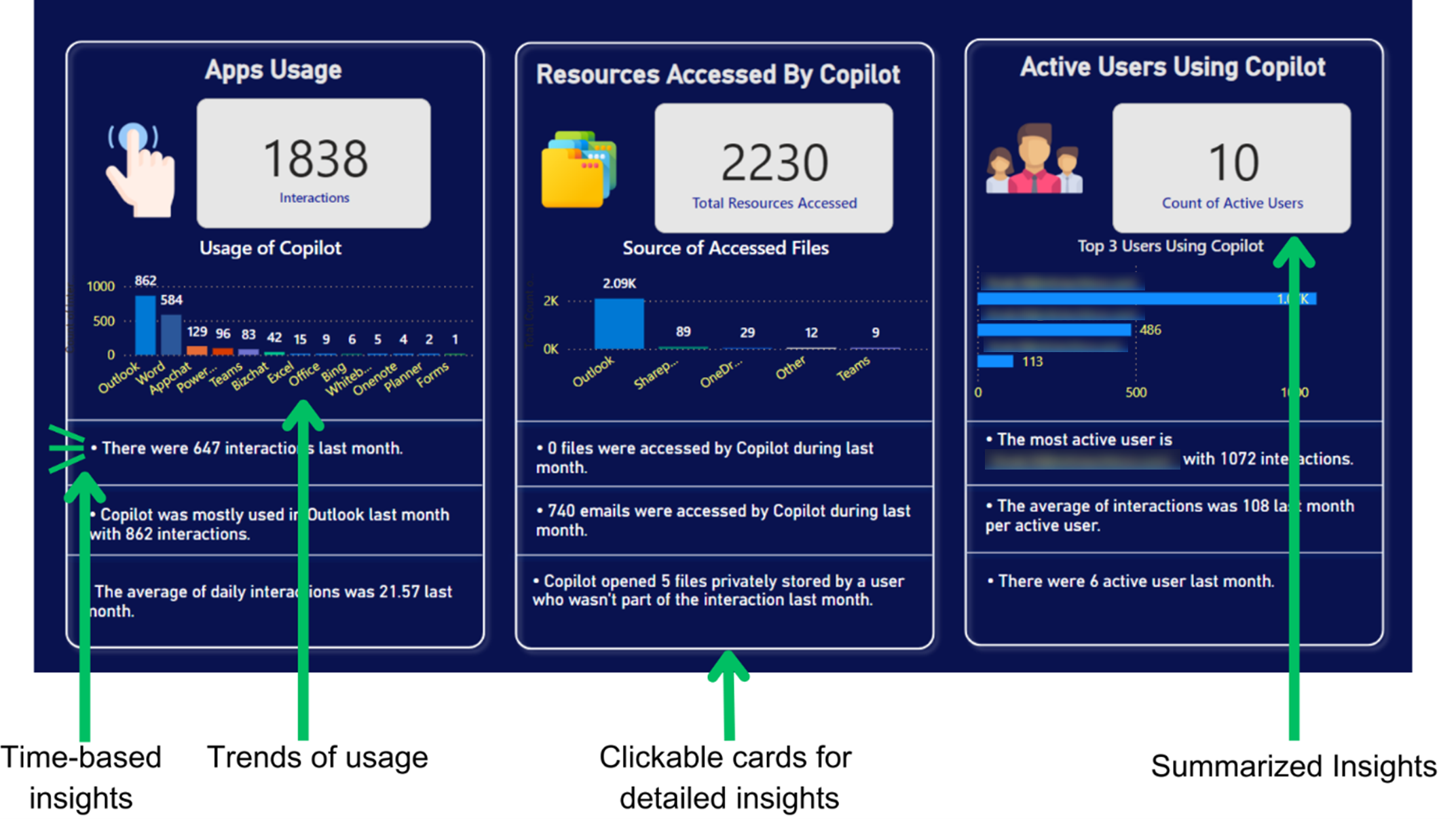
i-ARM reporting provides a comprehensive view of how Copilot is utilized across different departments and applications. This section explores the overall adoption rates and highlights which functionalities are most used, helping organizations understand where Copilot delivers the most value.
The overview page provides the following insights:
- Application Usage: Insights into which applications are frequently integrated with Copilot, guiding targeted improvements and training.
- User Engagement: Analysis of user interaction patterns, helping identify both power users and those who may need additional support.
Access Patterns and Security Insights
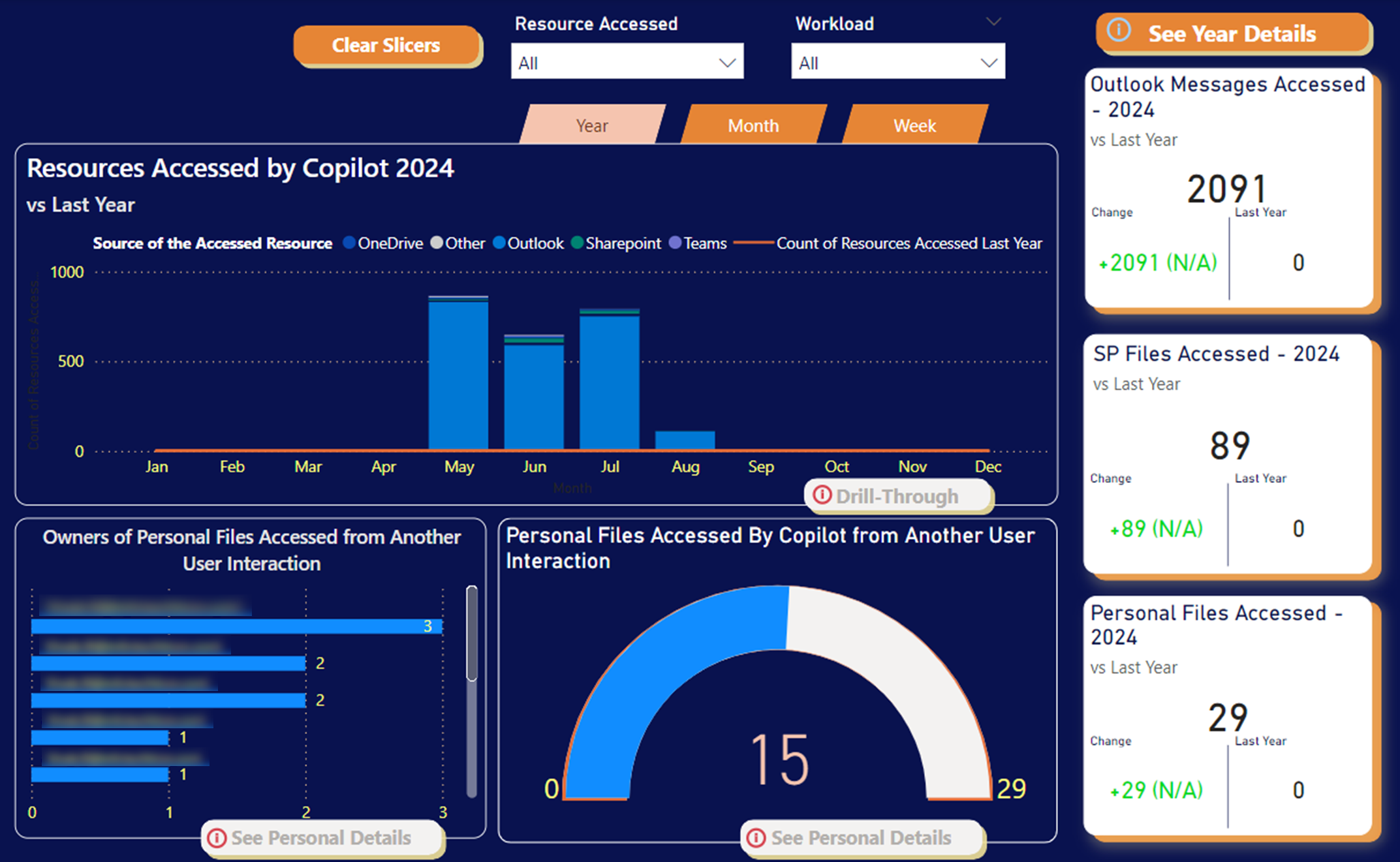
i-ARM plays an essential role in identifying how data is accessed and used, which is crucial for maintaining high data security standards.
Moreover, effective risk management is critical in the adoption of any new technology, specially AI. i-ARM reporting identifies potential risks and provides mechanisms to mitigate them, ensuring safe and compliant use of Copilot.
This report provides:
- Resource Access Overview: Monitoring what types of resources are accessed, providing insights into potential security vulnerabilities or compliance issues.
- Security and Privacy Monitoring: Tracking Copilot access to private information to ensure that data handling complies with legal and organizational standards.
- Risk Identification: Detect and address potential risks associated with unauthorized data access.
Detailed Analysis of Copilot Interactions
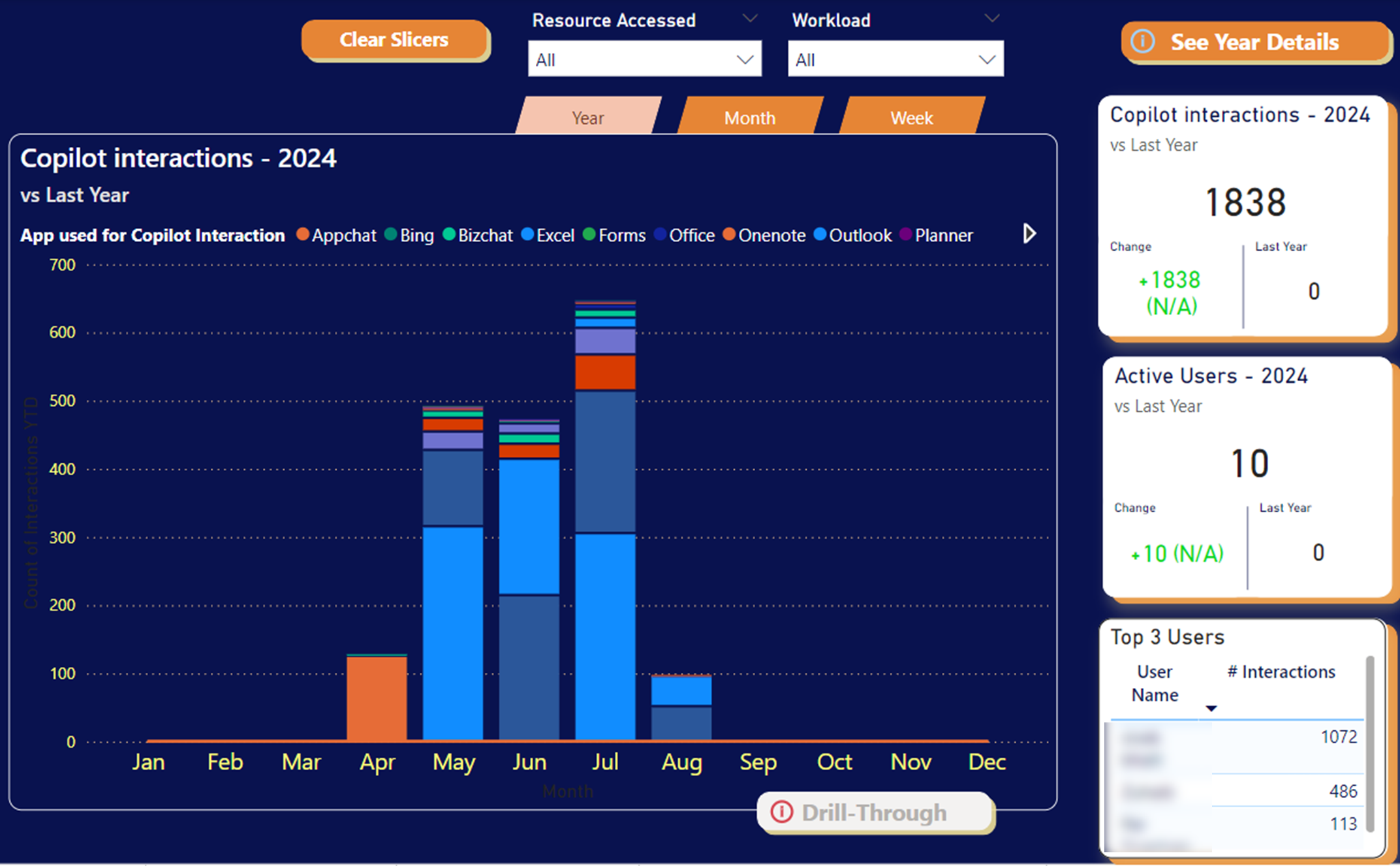
Through i-ARM reporting, companies can dive deep into the interaction data, revealing trends that help in fine-tuning the deployment strategies of technologies like Copilot.
- Interaction Trends: Understand how usage varies over time to optimize system performance during peak usage.
- Feature Utilization: Assess which Copilot features are most and least used to direct future development priorities and training programs.
User Engagement and Activity Patterns
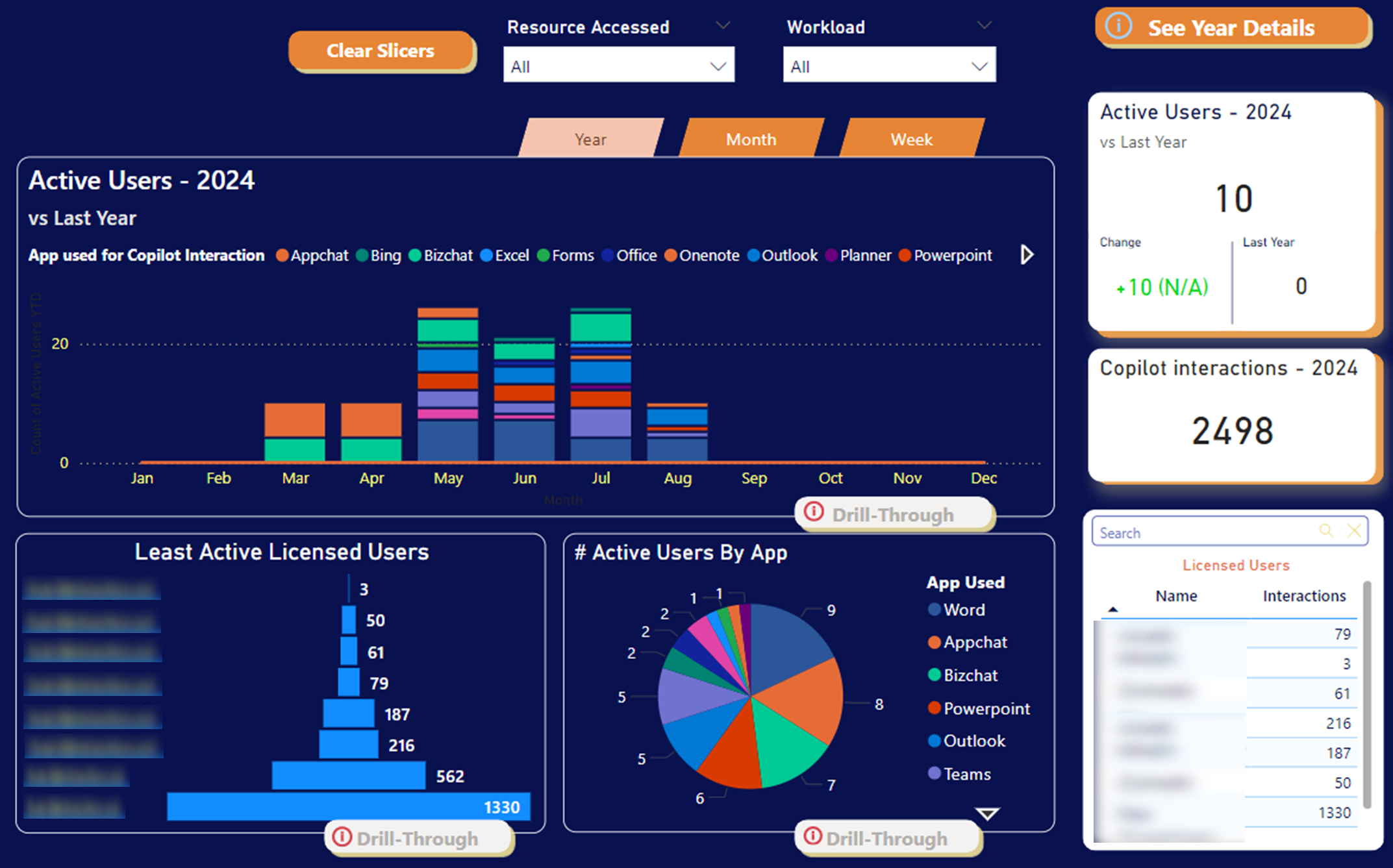
Analyzing engagement levels with Copilot helps in understanding its integration into daily workflows, providing valuable insights into its impact on business processes.
- Engagement Metrics: Evaluate how users interact with Copilot, identifying areas for increased adoption or additional training.
- User Behavior Analysis: Insights into user behaviors can help tailor the Copilot experience to better meet organizational needs.
Granular Data Insights from i-ARM Reporting
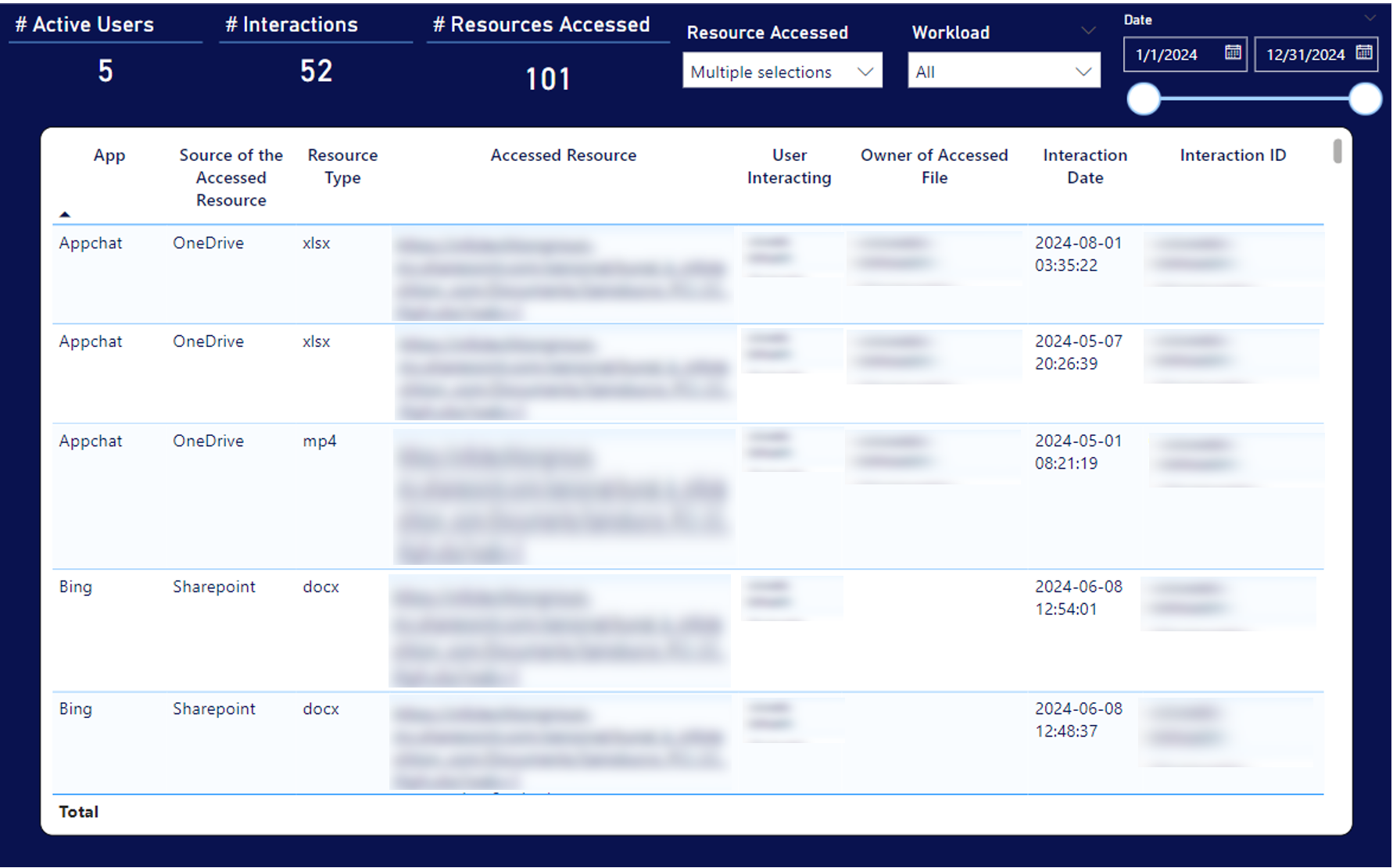
One of the key strengths of i-ARM reporting is its ability to present granular data that provides deep insights into how Copilot is being utilized within an organization. This level of detail is crucial for security oversight.
Detailed User Interactions
The report offers a granular view of user interactions with Copilot, including the specific actions taken and the applications used. This data allows managers to track exactly how Copilot is being leveraged in day-to-day tasks, identifying high-value uses and areas for improvement.
Comprehensive Access Logs
i-ARM reporting provides detailed access logs, showing which files and resources have been accessed by Copilot. This transparency is critical for maintaining control over sensitive data, ensuring that all access is monitored and recorded for security and compliance purposes.
Usage Patterns and Trends
The granularity of the data also extends to usage patterns, allowing for the identification of trends over time. By understanding these patterns, organizations can better predict future needs and make informed decisions about resource allocation and user training.
Upcoming Features in i-ARM Reporting
As organizations continue to adopt AI-driven tools like Copilot, the need for more detailed and actionable data is ever-increasing. To meet these demands, upcoming enhancements to i-ARM reporting will introduce several new features designed to provide even deeper insights and stronger security controls.
File Metadata Analysis
One of the most essential features is the inclusion of file metadata in the reporting. This will allow organizations to see not only which files were accessed by Copilot but also critical details like the last modified date. This information is vital for understanding the context of data usage and ensuring that the most up-to-date and relevant information is being utilized.
Sensitive Information Detection
To enhance security, i-ARM reporting will soon include the ability to detect and report on sensitive information within accessed files. Whether it’s personal information or confidential business data, organizations will be able to see exactly what type of data is being interacted with, enabling more precise risk management and compliance monitoring.
Dataset Comparisons
Another powerful upcoming feature is the ability to compare the files accessed by Copilot against the overall dataset of files available in the organization. This will help organizations identify any anomalies or patterns that could indicate unauthorized access or data misuse. For example, if Copilot is frequently accessing older, less relevant files, this could be a sign of inefficiency or a potential security risk that needs to be addressed.
Contact us today at contact@infotechtion.com to talk to our experts to discover more about i-ARM. We’re happy to help you take the next step.



