![]()
One of the notable features of Sensitivity Labels in Microsoft Purview is the ability to configure labels to apply encryption to files and emails. The primary purpose of this encryption is to manage access control for the labelled items, ensuring protection regardless of where the file or email resides or travels. While this advanced level of security is highly appealing, it also introduces practical considerations that extend beyond mere side effects.
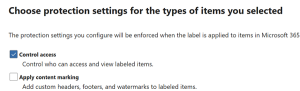
Encryption of Files and Emails is activated when you have selected Files and Emails to be in the scope of the sensitivity label and choose “Control access” as the protection setting (formerly called “Encryption”).
Note:
When encryption is activated, existing files at rest can also be encrypted, but this depends on how the sensitivity label is applied.

Auto-Labelling Policies (Service-Side Labelling)
When a label that includes encryption is applied to unencrypted files, they will be encrypted as part of this process. The encryption of existing files happens when the auto-labelling policy is executed.
Manual Labelling
User Action: If users manually apply a sensitivity label with encryption to existing files, those files will be encrypted immediately upon saving the changes.
When a an email is encrypted with a sensitivity label, all attachments will automatically inherit the encryption.
The subsequent step involves configuring the Access Control settings to ensure the appropriate level of protection. We will examine the possible implications of these settings on the typical Microsoft 365 knowledge worker during file and email operations.
Configure resulting permissions and other options
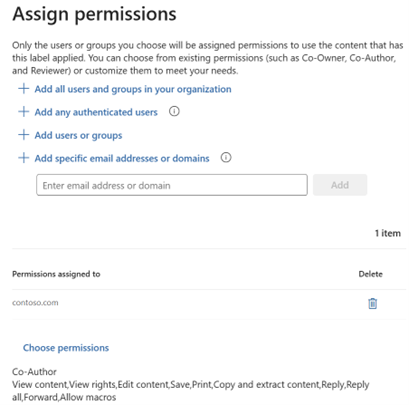
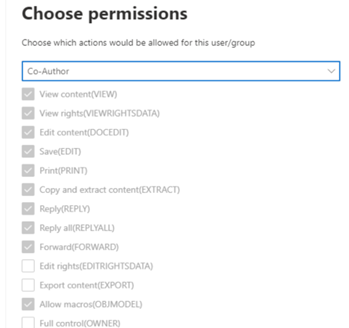
Or let the users decide when applying the label
More options:
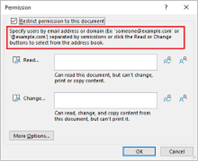
Allow offline access
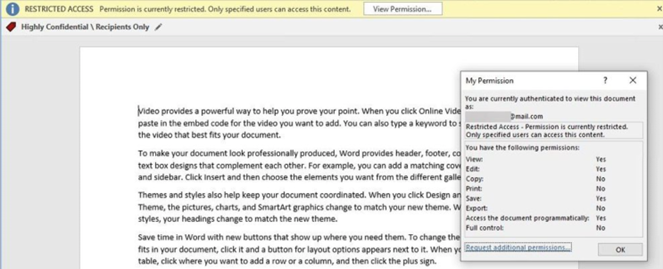
If you specify that labelled content is never available offline or is available offline only for a specified number of days, users must reauthenticate once this threshold is reached, and their access is logged.
Dynamic watermarks
When a user accesses a file with this label applied, their email address is dynamically inserted as a watermark on each page. This watermark is immutable and cannot be altered or removed by the user. (available exclusively with the ‘Assign permissions now’ option).
Impact of double encryption
Implementing Double Key Encryption (DKE) within a sensitivity label enhances security by utilising dual encryption keys: one key managed by the user and another key securely stored in Microsoft Azure. This approach offers robust protection for sensitive data. However, it is important to consider the following implications and limitations:
- Implications
- Double encryption ensures that even if one key is compromised, the data remains protected by the second key.
- Limitations
- Office documents that use double encryption do not support co-authoring and AutoSave features.
- Double encryption may not be compatible with all applications and services.
- The additional encryption layer can potentially impact the performance of data access and processing, especially for large datasets or high-frequency.
- Double Key Encryption (DKE) is entirely unsupported for Copilot for Microsoft 365 and MS Purview eDiscovery.
PDF implications
Inconsistencies on multiple fronts can arise depending on the application used to open the encrypted PDF file or the device/operating system (iOS, Windows, macOS, or Android). These inconsistencies may result in errors or even blocked files.
Consequently, several of our customers have opted to deactivate the ability to add sensitivity labels to PDF files entirely. This measure prevents PDFs from being encrypted if a previously applied label is later activated with encryption.
Note:
Microsoft has recently rolled out a new capability, allowing users authorised to access the file, to use the Microsoft 365 Mobile app to open and read PDF files protected by sensitivity labels in read-only mode.
Did you know?
- In addition to applying restricted access control, a sensitivity label can also be used to remove existing access/encryption settings.
![]()
If the user applying the label has the correct usage rights or role, any existing access control settings will be removed from the item.
- A sensitivity label remains persistently attached to the document, even after it is downloaded to an endpoint. Any efforts to remove or downgrade the label will trigger an event in the Activity Explorer.
So in short: Using encryption on MS Office files provides robust security, but it also comes with certain consequences and inconveniences.
Here’s a list to consider:
- Slower Access: Encrypted files may take longer to open and save due to the encryption and decryption processes.
- Increased Resource Usage: Encryption can consume more CPU and memory resources, potentially affecting overall system performance.
- Limited Co-Authoring: Features like real-time co-authoring in Office documents may be restricted or unavailable when encryption is applied.
- Sharing Restriction: Sharing encrypted files with external users can be more complex, requiring additional steps to grant access.
- Application Support: Not all applications support encrypted files, which can limit how and where the files can be used.
- Frequent Authentication: Users may need to reauthenticate frequently, especially if the files are set to be unavailable offline after a certain period.
- Regulatory Requirements: While encryption helps meet compliance requirements, it also necessitates strict adherence to key management and data.
- Audit Trails: Maintaining audit trails for encrypted files can be more complex, requiring detailed logging and monitoring.
Feel free to contact us at contact@infotechtion.com if you need any help configuring similar scenarios.



