![]()
On Board with CoPilot | Are you Modern Workplace Ready?
If you haven’t been living under a rock, chances are you’ve come across the buzz around CoPilot in the tech community, sparking curiosity, discussion, and even concerns about perceived risks. When you think about it, a solution that’s effective, quick and promises an immense productivity boost—what’s not to love? It’s like having a trusty ‘AI companion’ that makes our workdays a whole lot easier.
According to Forrester Research, an impressive 6.9 million US knowledge workers are projected to adopt Microsoft 365 CoPilot this year. While it swiftly summarises meetings, drafts reports in Word and automates the most mundane and administrative tasks—there are several factors you should contemplate before blindly onboarding the CoPilot journey and declaring yourself ’modern workplace ready’.
Navigating your Data | The pitfalls explained
CoPilot accesses content from Microsoft Graph, granting it access to organisational data. This access facilitates personalised assistance, but also poses the risk of accessing sensitive information unintentionally. What if CoPilot can find another employee’s salary details—perhaps your managers? (see example high-level workflow below).
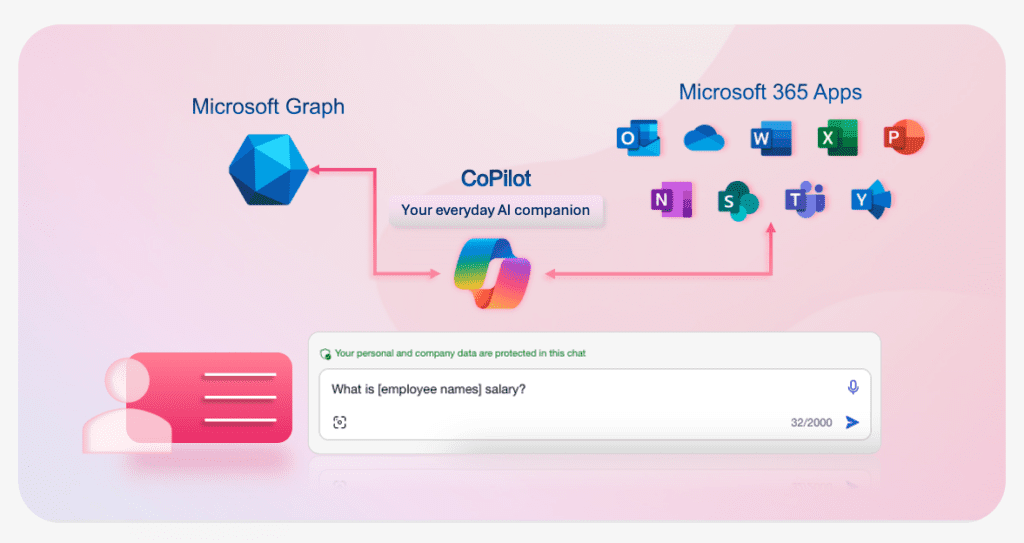
This occurs because CoPilot utilises Graph Data Connect, which analyses the content individuals have access to, including emails, files, meeting chats, and more. If this is the case, one might ponder the consequences of exposing an organisation’s top secrets, or if employee legal documents and medical information were leaked. The following section will address strategies for improving oversight and prevention, helping to avoid scenarios like this happening in the future.
According to Microsoft, CoPilot adheres to existing security, compliance, and privacy policies and unlike other AI models, it does not use your data to enhance its content or responses unless you explicitly allow it to.
Building an AI-Ready Workplace
By taking proactive steps to identify and minimise these risks, you can ensure a smoother AI-journey ahead. This is something that early adopters should think about when measuring their readiness level.
AI, CoPilot, and workplace/enterprise readiness all boil down to one thing: information readiness. How well do you know your information? Is it labelled, stored, and secured? How well do you enforce the least-privilege access principle? And that’s just the tip of the iceberg…
The Risks
Information Oversharing/Exposure
- While unintentional, there is a risk of CoPilot-generated content inadvertently sharing incorrect, old, or sensitive data.
- When implementing CoPilot, collaboration links and mislabelled or unlabelled files pose potential security, privacy, and compliance risks.
Insider Risk
- Could potentially gain unauthorized access to sensitive data due to the two primary risks mentioned. Consequently, they might misuse CoPilot and exfiltrate business-confidential information.
Over-permissioning of users
- Many users within the tenant may have excessive permissions, which can lead to situations where CoPilot inadvertently exposes data that users should not have access to or are unaware, and they should avoid. For instance, CoPilot can access ‘Anyone’ sharing links.
Best Practices
Review Access and Control Policies to Prevent Over-permissioning:
Stay proactive with access controls: Think ‘just enough’ and ‘least privilege.’ That way, only the right users can get their hands on the right data. For example, consider aspects such as link access (including anyone links) and SharePoint permission settings.
Label, Automate and Classify your Data: Rigorous management and automated tagging of sensitive information are crucial to uphold security standards, while also adhering to storage limitations and reducing data usage. Consider this scenario: if a document is mistakenly labelled as “public” and contains highly sensitive business information, CoPilot could inherit that label. (See here).
- As in the above scenario the label is incorrect, it could lead to broader access by unintended recipients, as well as inaccurately labelled data when using CoPilot.
Automate data lifecycle management workflows: Redundant, obsolete, and trivial (ROT) data, as well as temporary files and duplicates should be efficiently removed. If CoPilot uses old, unnecessary data, it won’t produce precise or up-to-date content. It’s like trying to make a gourmet meal with stale ingredients—definitely not a recipe for success!
Other Important Considerations:
- Technical prerequisites: Microsoft outlines several essential technical prerequisites that should be taken into account. For instance, Microsoft 365 CoPilot users must be assigned a Microsoft 365 E3 or E5 license and have an Azure Active Directory account to be eligible. You can find further guidance from Microsoft
- Who gets the licenses? While around £25 a month isn’t exactly wallet-crushing, if you start assigning licenses like confetti you might end up with a rather large bill. That’s where “personas” come in handy. Essentially, you need to determine who will benefit the most from it and who would require it to perform their job more effectively and efficiently.
- Management and Adoption Strategy: An IT management and an adoption strategy are essential for effectively implementing CoPilot, ensuring user engagement, and promoting safe usage with confidential data.
- How is it being used? CoPilot’s Insights Dashboard provides visibility into user adoption, usage patterns, and key metrics, including time saved. This invaluable data assists in calculating the return on investment (ROI).
Conclusion
Before an organisation declares itself ’modern workplace ready’, several things come into play. To recognise its value and manage risks effectively, it’s important to set up a solid foundation of governance and security. Plus, don’t forget to educate your users on how to use it!
Need help getting ready for CoPilot? Contact us at contact@infotechtion.com to learn more.



