![]()
Since its inception in 2020, Microsoft Purview Insider Risk Management (IRM) has been the subject of extensive discourse and analysis. For those seeking a concise overview: IRM serves as an advanced analytical tool that synthesises diverse signals to pinpoint potential insider threats, whether they stem from intentional misconduct or inadvertent actions, encompassing intellectual property theft, data breaches, and security infractions.

With the widespread deployment of Adaptive Protection within Microsoft Purview, we are leveraging machine learning algorithms to discern the most pressing risks. This enables us to proactively and dynamically enforce protective measures, integrating them seamlessly into DLP, Conditional Access and Data Lifecycle Management (DLM) policies as part of the broader IRM framework. The term ‘dynamically’ implies that activities classified as ‘high-risk’ will trigger the enforcement of more stringent DLP actions, thereby diminishing the interval necessary to detect and address potential threats effectively. This approach will facilitate the implementation of robust controls for users presenting high-risk behaviours, while allowing others to sustain their productivity unimpeded.
Specifically, Conditional Access policy controls constantly adjust, so when a user’s insider risk level changes, an appropriate policy is dynamically applied to match the insider new risk level. For DLM, IRM automatically preserves deleted data of high-risk users for 120 days with a retention label policy.
Insider risk levels
IRM provides a tri-tiered framework of insider risk levels (Elevated, Moderate and Minor), each with predefined criteria; however, these parameters are fully customisable to meet specific organizational needs. You can select one, two or all three in a policy rule.

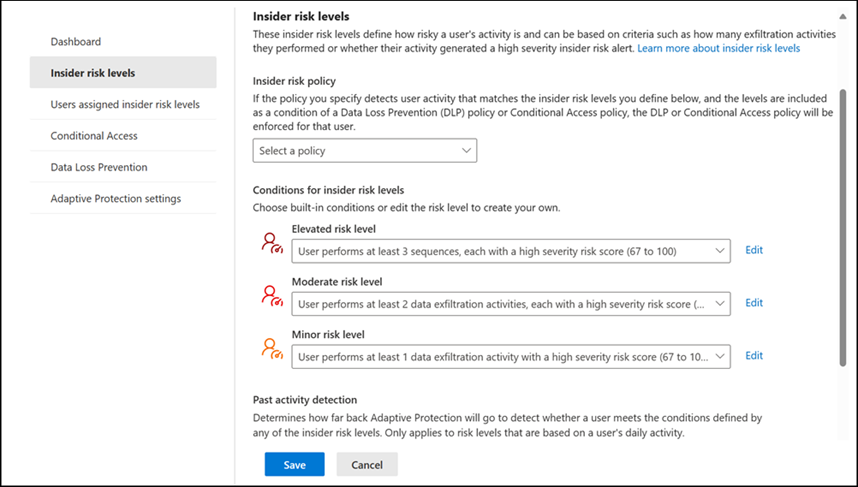
Adaptive Protection in Data Loss Prevention

Let’s think of a specific example here:
Consider the case of a financial analyst within an enterprise, tasked with managing confidential financial information. Ordinarily, the analyst’s data access and manipulation are regulated by standard DLP policies. However, should there be detection of anomalous activities—such as file access attempts during irregular hours or the transfer of substantial data volumes to an external device—the system promptly escalates the user’s risk status.
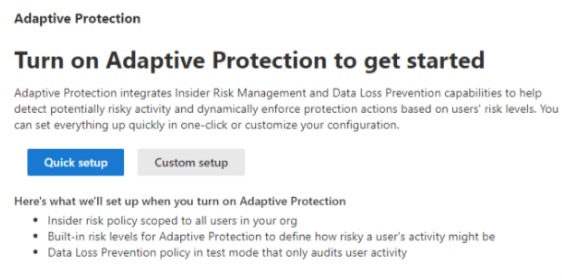
Remember to turn on first Adaptive Protection in the Insider Risk Management settings
Quick setup configuration
If quick setup is used to configure Adaptive Protection in insider risk, DLP policies are created automatically . This expedient configuration establishes a singular policy for Teams and Exchange Online, which encompasses two distinct rules: one tailored for the elevated risk profile, and another addressing moderate and minor insider risk levels. Additionally, a separate policy with two analogous rules is created for device management.
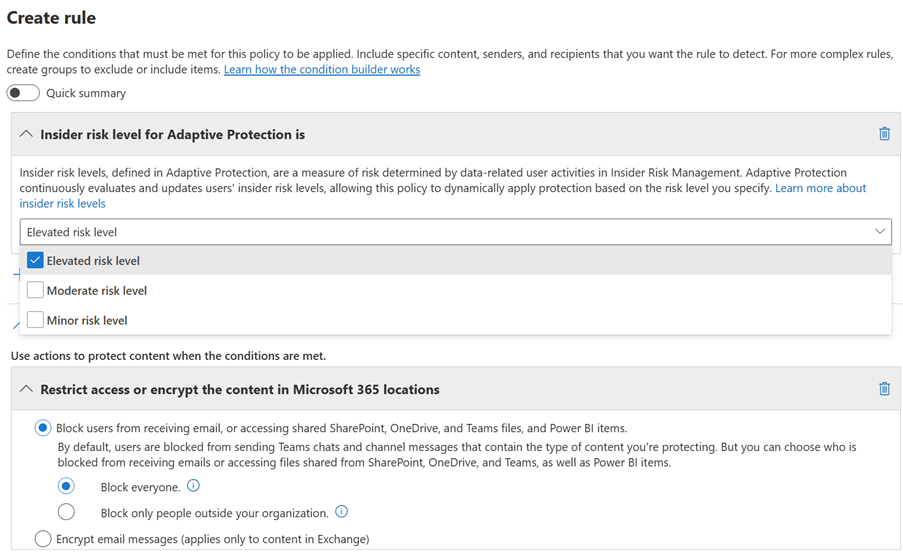
Manual configuration (using a DLP policy)
Envision a DLP policy composed of two distinct rules: the first applies to users categorised under Minor or Moderate risk levels, prompting a policy tip upon attempts to disseminate information falling within the DLP’s purview. The second rule, however, is designed for users assessed with an Elevated risk level, and it precludes the sharing of such content entirely.
You manually configure an adaptive protection DLP policy just like you would configure any other policy:
Microsoft 365 insider risk management license requirement
- Microsoft 365 E5
- Microsoft E5 compliance add-on
- Insider Risk add-on for Microsoft 365
Note: Any user who needs to be investigated also requires any one of the above licenses.
Feel free to contact us at contact@infotechtion.com if you need any help configuring similar scenarios.



