Understanding Data Loss Prevention with Microsoft Purview
In an era where data underpins critical business decisions, enterprises must adopt robust governance frameworks to manage, protect, and extract value from their information assets. Microsoft Purview offers a unified platform for data governance—combining discovery, classification, lineage, and policy enforcement—to help organizations achieve compliance, mitigate risk, and foster data-driven innovation. By automating governance workflows and providing rich metadata insights, Purview enables teams to collaborate more effectively while maintaining stringent security and privacy standards
Table of Contents
- Why Microsoft Purview Has Become the Enterprise Standard
- Core Architecture: Data Map + Unified Catalog
- Governance Vision & Stakeholder Alignment
- Designing Domains, Collections & Network Topology
- Implementation Roadmap
- Ten Best Practices
- Seven Common Pitfalls & Mitigations
- Measuring Success
- Future Trends: AI, Fabric, Zero-Copy Governance
- Quick-Start Checklist
Why Microsoft Purview Has Become the Enterprise Standard
Every enterprise now wrestles with petabytes of structured, semi-structured, and unstructured data spread across SaaS applications, multiple clouds, legacy data centers, and a growing number of AI-enabled workplace tools. At the same time, regulatory oversight is intensifying: the EU’s Digital Operational Resilience Act (DORA) enters force in 2025; the U.S. SEC’s cyber-incident disclosure rule is now live; and more than 150 jurisdictions have active or draft privacy laws. Boards therefore demand provable governance, continuous compliance, and demonstrable data value-creation.
Microsoft responded by merging its disparate security, compliance, and catalog services into Microsoft Purview—a single control plane that discovers, classifies, catalogs, protects, and monitors data wherever it lives. Because it is natively integrated with Microsoft 365, Azure, Entra ID, and the new Microsoft Fabric lakehouse, Purview gives CIOs and CISOs end-to-end visibility without expensive third-party connectors. IDC estimates that more than 1 800 enterprises moved to Purview in the first year of general availability and that deployments grew 400 percent year-over-year in 2024. Early adopters report a 60 percent reduction in manual compliance effort, a 30 percent cut in audit preparation time, and materially faster time-to-insight because analysts can trust cataloged data.
Core Architecture: Data Map + Unified Catalog
| Engine | What It Does | Why It Matters |
|---|---|---|
| Data Map | Registers and scans on-prem, multicloud, and SaaS sources; stores technical metadata. | A continuously refreshed inventory enables lineage, impact analysis, and DSPM (Data Security Posture Management). |
| Unified Catalog | Presents assets, lineage graphs, classifications, and business-glossary terms in a self-service portal. | Knowledge workers can quickly discover trusted data; stewards can enrich assets. |
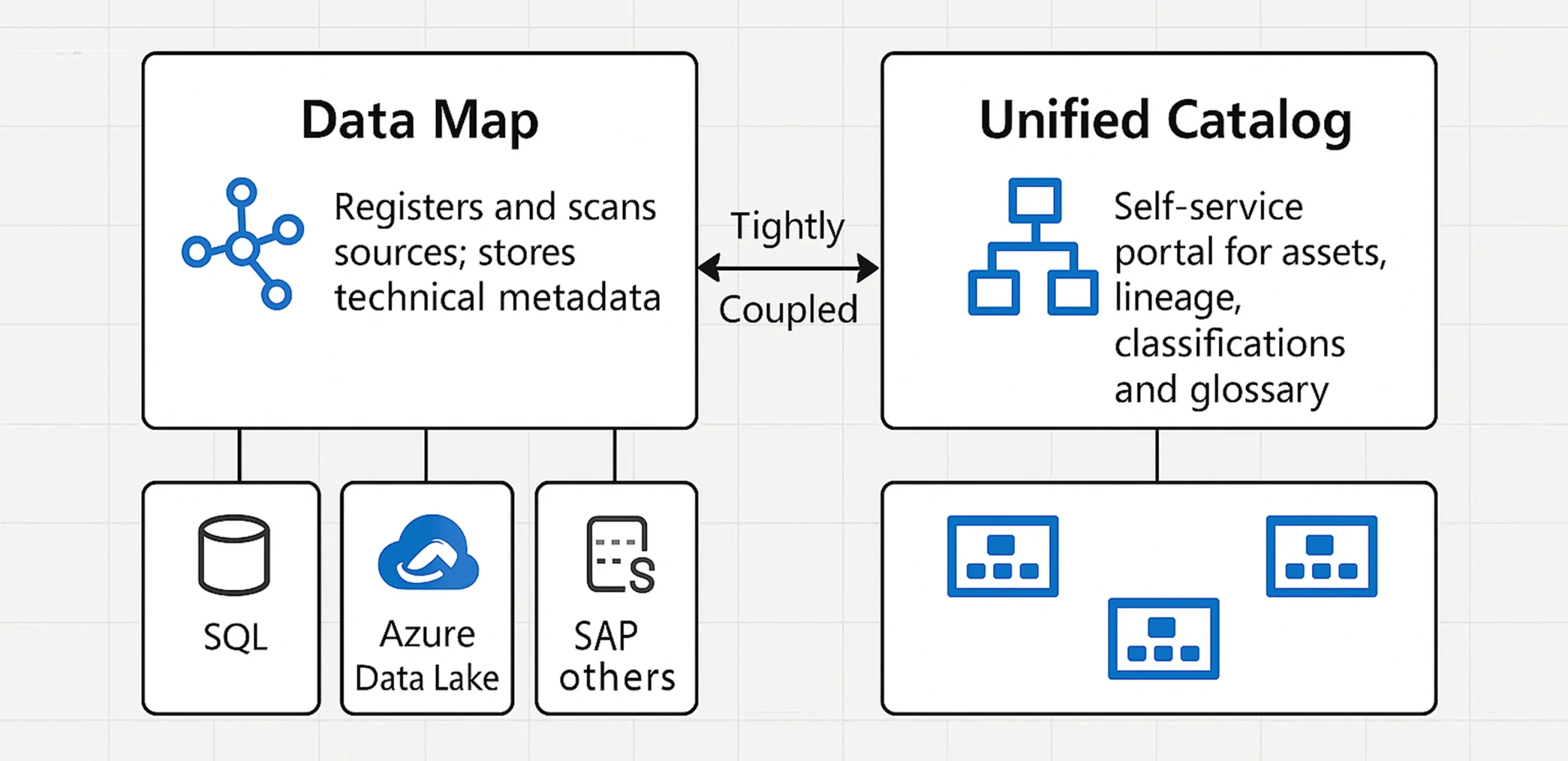
On top sit Data Estate Insights and Catalog Adoption dashboards, which surface KPIs such as asset coverage, classification precision, and user engagement; and DSPM for AI, which flags sensitive data exposure in Microsoft Copilot prompts and other generative-AI workflows.
Governance Vision & Stakeholder Alignment
Successful implementations start with a vision that links Purview outcomes to business objectives:
“Lower audit cost by 40 percent, cut data-request cycle time to 48 hours, and enable privacy compliance in all operating regions.”
Next, map the stakeholders:
- Executive Sponsor – secures budget and resolves conflicts.
- Data Owners – accountable for data quality and policy adherence.
- Data Stewards – curate metadata, certify data sets, manage glossary.
- Data Custodians / IT – configure connectors, manage Integration Runtime, monitor scans.
- Security & Compliance – define classification taxonomy, retention schedules, DLP rules.
- Analytics / AI Teams – consume cataloged data; surface lineage gaps.
Jointly agree on success metrics—for example, percentage of catalog coverage, classification accuracy, or policy-violation mean time-to-remediation (MTTR). Without measurable goals, governance devolves into PowerPoint.
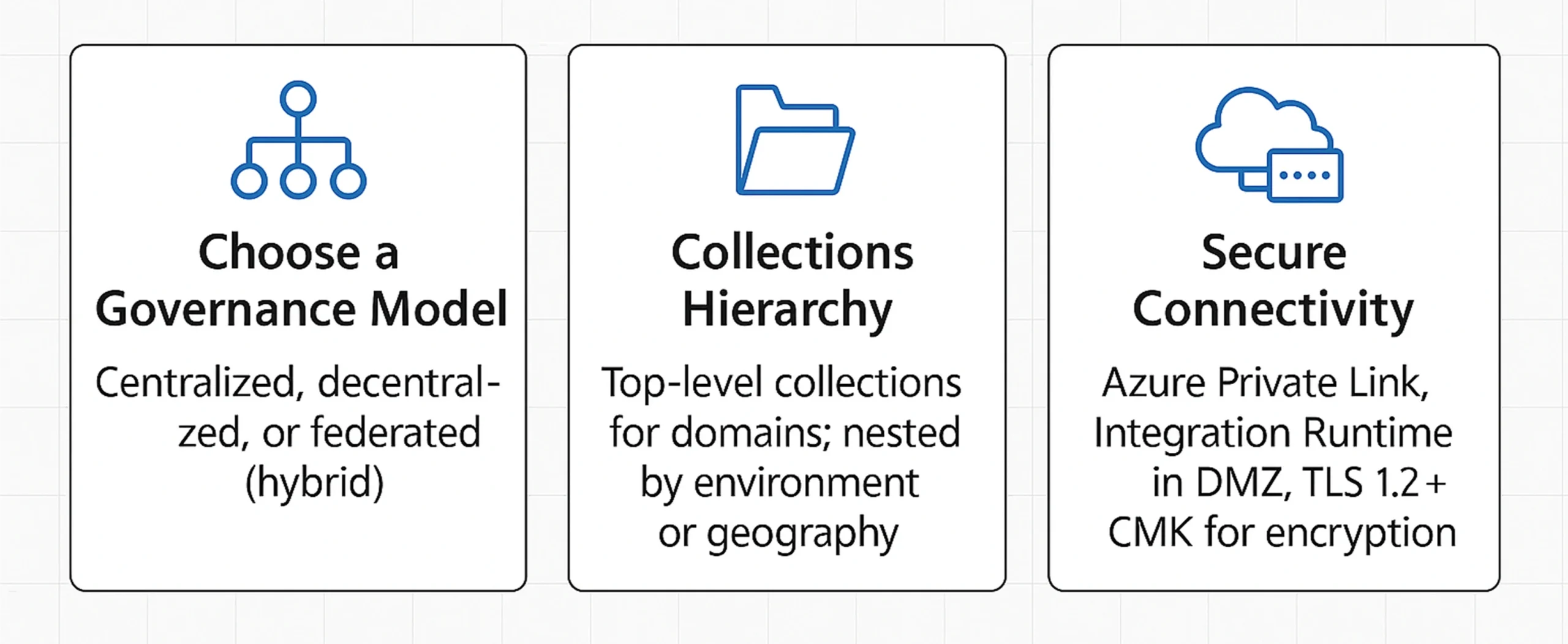
Designing Domains, Collections & Network Topology
Choose a Governance Model
Microsoft documents three archetypes: centralized, decentralized, and federated (hybrid). In centralized models, a data-governance office controls all collections; in decentralized setups, business units govern their own; most enterprises adopt a federated compromise—central guard-rails, local stewardship—which balances innovation and control.
Collections Hierarchy
Create top-level collections for major domains such as Finance, HR, R&D, or Customer360. Nest environments (Prod, QA) or geographies (EU, US) underneath to observe data-residency laws.
Secure Connectivity
- Use Azure Private Link so catalogue and scan traffic never exits the Microsoft backbone.
- Deploy Purview Integration Runtime (IR) in a DMZ to reach legacy sources; whitelist only required ports.
- Enforce TLS 1.2+ and leverage customer-managed keys (CMK) for at-rest encryption when industry regulations (e.g., FedRAMP High) demand exclusive key control.
Implementation Roadmap
| Phase | Time-box | Deliverables |
|---|---|---|
| 1. Assessment | Weeks 1-2 | Inventory data sources; map regulations; baseline maturity. |
| 2. Foundations | Weeks 3-4 | Create Purview account, resource group, private endpoints; assign RBAC; deploy IR. |
| 3. Pilot Scan | Weeks 5-6 | Register high-value sources (e.g., SAP HANA, SharePoint Online); run baseline scan; verify classification accuracy. |
| 4. Classification Sprint | Weeks 7-9 | Enable built-in classifiers; develop three custom Trainable Classifiers; finalize sensitivity-label taxonomy. |
| 5. Retention & DLP | Weeks 10-12 | Publish retention labels, disposition reviews, and DLP policies; integrate with Power Automate for alerts. |
| 6. Adoption Wave | Weeks 13-18 | Train stewards; run catalog evangelism workshops; crowd-source glossary terms. |
| 7. Scale-out | Months 5-12 | Onboard remaining sources, enable eDiscovery Premium and DSPM; automate health reports. |
Many enterprises run phases 1-5 in a single quarter to demonstrate ROI quickly, then iterate. Purview’s REST and ARM/Bicep APIs let teams treat governance artifacts as code, so scanners, roles, and policies can be version-controlled and promoted through dev/test/prod like any modern application.
Ten Best Practices
- Start Small, Scale Fast
A well-scoped pilot (one domain, two sources) uncovers connector quirks, refines taxonomy, and yields early success stories. - Federate Stewardship
Central data-office defines policies; domain stewards own curation. This mirrors “data-mesh” thinking while satisfying auditors. Microsoft Learn - Exploit Trainable Classifiers
Regex patterns struggle with free-text or non-Latin scripts. Upload 50–200 labeled samples to create ML classifiers that learn your domain language. - Automate Everything
• Schedule scans nightly or weekly.
• Use Power Automate to ping owners on policy violations.
• Auto-apply labels based on content and location rules. - Treat Governance as Code
Store Purview collections, roles, scans, and label policies in Bicep or Terraform; enforce pull-request reviews. Drift detection keeps prod aligned with templates. - Integrate SIEM & XDR
Stream Purview audit logs to Microsoft Sentinel; correlate DLP alerts with endpoint/identity telemetry for faster incident triage. Microsoft Learn - Gamify Catalog Adoption
Publish league tables of glossary contributions; award “Data Hero” badges. Culture change beats mandate. - Quarterly Rule Review
Business processes evolve; check classifier precision/recall every quarter and retire obsolete labels. - Embrace Zero-Trust
Use Entra ID Conditional-Access + Purview sensitivity labels + continuous access evaluation. Every request is verified; permissions adapt to risk. - Leverage Data Estate Insights
Governance leaders get health scores across coverage, policy compliance, and catalog usage. Use the dashboards in steering-committee meetings to prioritize next sprints.
Seven Common Pitfalls & Mitigations
| Pitfall | Impact | Mitigation |
|---|---|---|
| Over-Classification | “Confidential” label everywhere → alert fatigue → users ignore. | Pilot rules on sample sets; use confidence thresholds; prune weekly. |
| Network Firewalls Block Scans | Scans fail; catalog gaps. | Engage network team early; document IP/ports; test with staging IR. |
| RBAC Sprawl | Too many Data Curators = privilege creep. | Map roles to HR job codes; quarterly access reviews. |
| License Mismatch | Auto-labeling and eDiscovery Premium need E5/Add-on; unexpected cost overruns. | Run an E3 vs E5 ROI assessment before rollout. |
| Steward Burn-out | Manual tagging backlog; catalog stagnates. | Automate lineage, crowd-source glossary, rotate stewardship duties. |
| Ignoring AI Workflows | Copilot prompts log sensitive data; regulator fines. | Enable DSPM for AI; block high-risk prompts; apply redact/mask rules. |
| No Post-Go-Live Monitoring | Drift, stale scans, orphan labels. | Schedule Data Estate Insights refresh (weekly by default) and send health reports to exec sponsor. |
Measuring Success
Purview ships Catalog Adoption Insights and Data Estate Insights dashboards, exposing KPIs such as:
| KPI | Target | Feature |
|---|---|---|
| Asset Coverage | ≥ 90 % of inventoried systems scanned | Data Estate Summary |
| Classification Precision | ≥ 85 % precision / ≥ 80 % recall | Classification Review |
| Policy-Violation MTTR | < 8 hours | DLP Alerts + Power Automate |
| Monthly Active Catalog Users | ≥ 60 % of target personas | Adoption Dashboard |
| Audit-Ready Score | ≥ 95 % | Data Estate Insights |
Export these metrics via REST API to your BI tool, or pin dashboards directly in Teams for transparency.
Future Trends: AI, Fabric, Zero-Copy Governance
- Policy Copilot – A forthcoming feature will let stewards write plain-language rules (“retain invoices seven years, then delete”) that Purview converts to JSON policies.
- Zero-Copy Governance – With Microsoft Fabric’s OneLake, Purview lineage will natively track Delta tables and shortcuts, enabling policy enforcement without moving data.
- Cross-Cloud Connectors – Preview connectors for AWS Glue, Snowflake, and SAP Datasphere will close multicloud gaps.
- Privacy-Enhancing Labels – Differential-privacy and confidential-compute tags will become first-class citizens, surfacing in Data Security Posture dashboards.
- Real-Time Lineage – Kafka streams will soon appear in lineage views, giving risk teams second-by-second insight into sensitive data flows.
Quick-Start Checklist
Executive sponsor named, budget secured
Governance committee chartered
Purview account & Private Link deployed
Collections hierarchy approved
Integration Runtime installed and tested
Baseline scan completed (≥ 1 000 assets)
Sensitivity-label taxonomy ratified
First three trainable classifiers in QA
Retention/DLP policies published
Dashboards shared with stakeholders
Quarterly review cadence on calendar
Implementing Microsoft Purview is not a checkbox exercise—it re-engineers how your organization discovers, secures, and leverages data. By coupling a clear governance vision with Purview’s automated classification, lineage, and policy-enforcement capabilities, enterprises can shrink audit costs, reduce breach risk, and unlock analytic value. Follow the roadmap, embrace the ten best practices, and sidestep the seven pitfalls outlined above. Then continually measure, iterate, and evolve as new AI-driven capabilities, zero-copy architectures, and regulatory mandates emerge. With Purview as your governance backbone, your data estate becomes not a liability but a launchpad for innovation.
Get in touch today.
For any questions

© 2026 ALL RIGHTS RESERVED
Sitemap
