![]()
What Is Zero Trust?
At its core, Zero Trust is a paradigm shift—a departure from the old guard of cybersecurity. It rejects the notion of inherent trust, whether bestowed upon users, devices, or applications. Instead, it champions a relentless pursuit of verification. This transformative concept emerged from the cybersecurity community in an age where trust is no longer a given.
Why Zero Trust?

Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the hybrid workplace, and protects people, devices, apps, and data wherever they’re located. That is why the Zero Trust principle should extend beyond the Open Systems Interconnection (OSI) level into the Data Security landscape.
This article will make you understand what Microsoft Purview can offer as an integrated solution to construct a framework encompassing Zero Trust principles for data security and compliance.
Let’s delve into the challenges of Zero Trust
In an increasingly interconnected digital landscape, safeguarding sensitive data has become paramount. By entering the Zero Trust Principle, we unveil a security strategy that has been proven essential when organizations pro-actively plan to grant their users access to the promising Microsoft Copilot platform

Original key principles of Zero trust
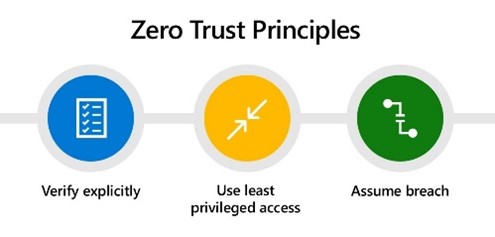
- Verify Explicitly: Gone are the days of implicit trust; every access request must be explicitly validated.
- Use Least Privilege Access: Limit user access to the bare essentials. Implement just-in-time (JIT) and just-enough-access (JEA) policies.
- Assume Breach: Adopts a “trust no one” mentality.
Zero Trust and Data Security

Now, let’s explore how Zero Trust principles intersect with data security
Use the capabilities from Microsoft Purview to help you discover, classify, protect, and govern sensitive information wherever it lives or travels.

Know your data
To gain comprehensive insights into your data landscape and effectively identify sensitive information within your hybrid environment, leverage the following capabilities:
- Sensitive information types to identify sensitive items by using built-in or custom regular expressions, or a function.
- Trainable classifiers to identify sensitive items by using examples of the data you’re interested in rather than identifying elements in the item.
- Data classification provides a graphical identification of items in your organization that have a sensitivity label, a retention label, or have been classified and the actions your users are taking on them.

Protect your data
Sensitivity labels can apply protection actions that include encryption, access restrictions, and visual markings to increase awareness and compliance.
- Empower users to manually label files and emails with clear instructions, ensuring they effectively convey the sensitivity of the content.
- Use Auto-label policies as a predefined set of rules or conditions to automatically apply classification labels to files, documents, or emails based on specific criteria.
Prevent data loss
Microsoft Purview Data Loss Prevention (DLP) can help protect your organization against unintentional or accidental sharing of sensitive information both inside and outside of your organization.
In a Data Loss Prevention Policy, you:
- Define the sensitive information you want to monitor for, like financial, health, medical, and privacy data.
- Where to monitor, like Microsoft 365 services or Windows and macOS devices.
- The conditions that must be matched for a policy to be applied to an item, like items containing credit card, driver’s license, or social security numbers.
- The actions to take when a match is found, like audit, block the activity, and block the activity with override.
Detect and act on risk activities with Insider Risk Management
Microsoft Purview Insider Risk Management (IRM) effectively tackles significant data security challenges, particularly those related to insider threats. This solution empowers organizations to identify, investigate, and respond to both intentional and unintentional activities occurring within their ranks. By leveraging adaptive protection features, it automatically optimises data security, safeguarding sensitive organizational data across various environments, including clouds, devices, and platforms.

Restrict communication and collaboration between users with Information Barriers

Microsoft Purview Information Barriers (IB) serves as a compliance solution that enables the restriction of two-way communication and collaboration between distinct groups and individual users within Microsoft Teams, SharePoint, and OneDrive. This solution is particularly valuable in highly regulated industries, as it helps mitigate conflicts of interest and safeguard sensitive internal information.
Remember: Trust no one implicitly; verify everything explicitly. Zero Trust isn’t just a buzzword—it’s a fundamental shift toward a more secure digital future.
Feel free to contact us at contact@infotechtion.com if you need any help configuring similar scenarios.



