Data Loss Prevention for Copilot: 3 Essential Policies Every Organization Needs in 2025

![]()
Whether you plan on implementing Microsoft 365 Copilot in your organization or you have already implemented it, Copilot security should be your top concern. With Copilot you can access and process vast amounts of your organizational data, which offers tremendous productivity benefits but also introduces new security challenges that you need to address proactively. The […]
How to avoid data breaches

![]()
Data breaches rarely happen the same way twice. Some are driven by malicious insiders, others by external hackers, careless employees, or even well-intentioned staff experimenting with new AI tools. What they all have in common: the cost to the business can be devastating. Below are four real-world style scenarios that show how breaches often occur […]
Smart Coding with AI: A Guide for Teams to Adopt Responsibly

![]()
Artificial Intelligence is no longer just analyzing our code, but it’s writing it. AI coding assistants like GitHub Copilot, Cody, and others are quickly becoming companions to developers everywhere. They promise faster delivery, cleaner syntax, and fewer late nights fixing bugs. But while the idea of “a robot pair programmer” sounds attractive, it also raises new questions: how […]
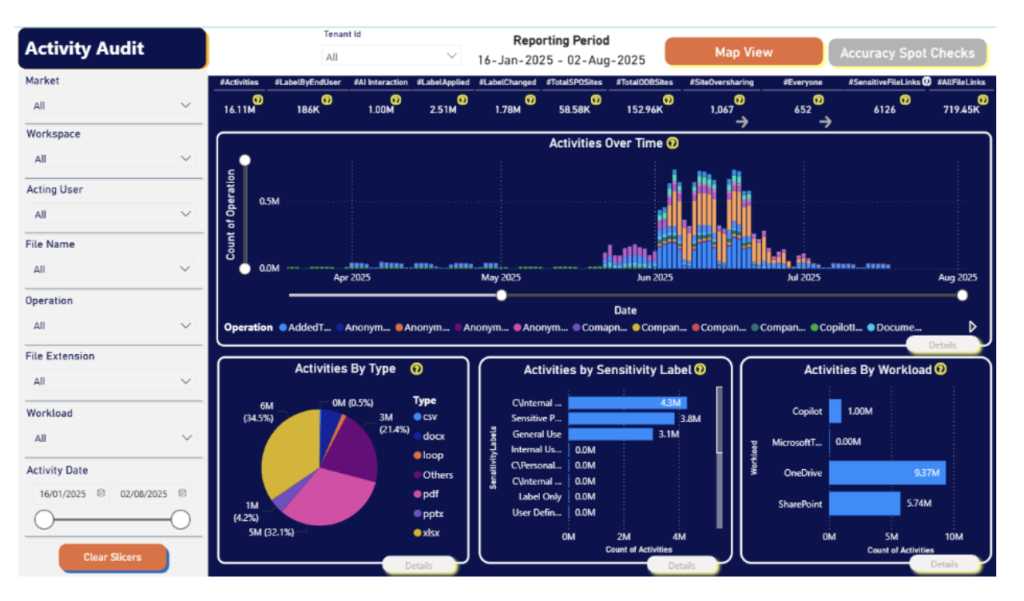
Turning Audit Pain into Audit Readiness: How to Simplify Compliance
![]()
IT security audits are meant to validate that an organization’s information assets are secure and compliant. Regulators, boards, and customers expect assurance that risks are managed against standards and regulations such as ISO/IEC 27001, NIST SP 800-171/53, PCI DSS, HIPAA, and GDPR. For CISOs, audits should showcase security maturity. Instead, they often become a repetitive, […]
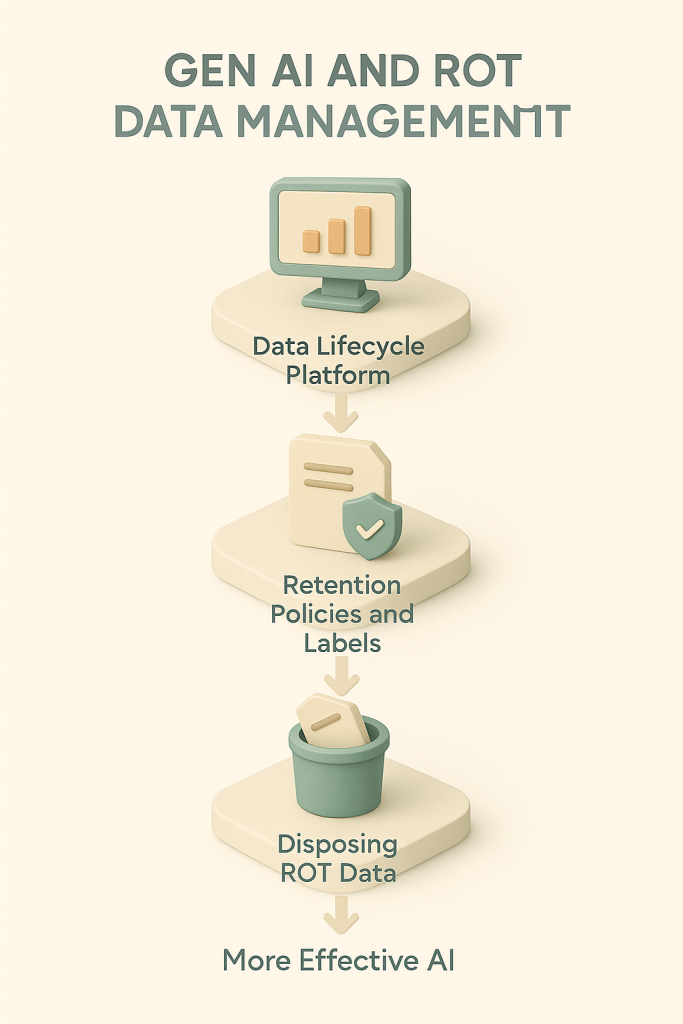
Microsoft Copilot, Gen AI and ROT Data Management
![]()
Microsoft Copilot, Gen AI and ROT Data Management The whitepaper Gen AI and ROT Data Management, co‑authored by Infotechtion’s Vebjørn Krågebakk, and BI Norwegian Business School Professors Christoph Lutz and Samson Yoseph Esayas makes a clear case: if you want reliable, safe and efficient Gen AI, you need disciplined and consistent data lifecycle management and […]
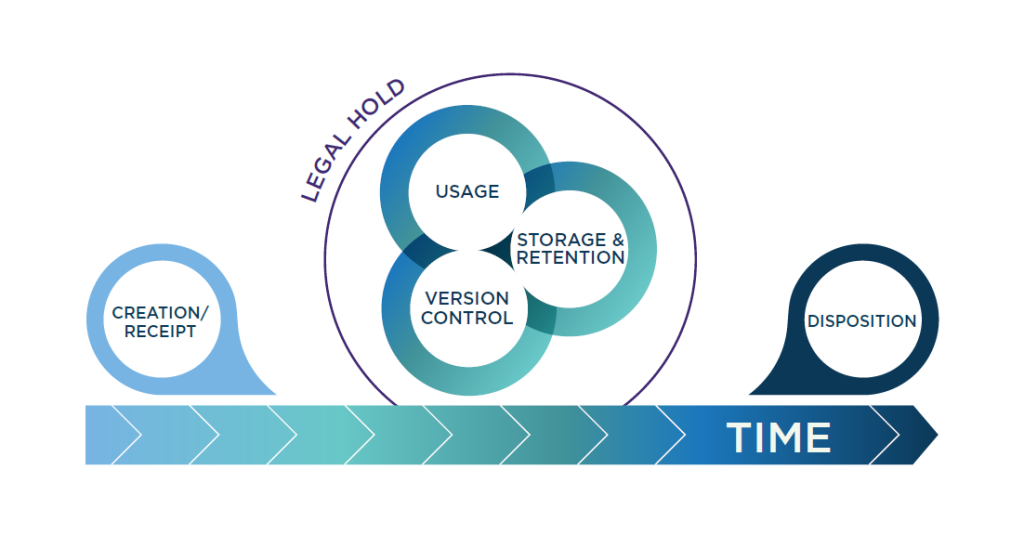
Foundations of Retention: The Essentials of a Fit-for-Purpose Retention Schedule
![]()
A well-designed retention schedule is the cornerstone of any effective records management policy. It’s not just a compliance tool—it’s a strategic asset that supports defensible disposition, reduces risk, and enables smarter data lifecycle management. Yet, many organizations struggle to make their retention schedules truly fit-for-purpose. This post outlines the practical steps to build (or improve) […]
Unlocking the Power of Microsoft Purview Device DLP Policies

![]()
Data Loss Prevention (DLP) is a critical component of modern security strategies, especially with the explosion of remote work and the proliferation of endpoints. While DLP policies for cloud services like SharePoint and OneDrive are well-known, Microsoft Purview Device DLP offers distinctive capabilities that extend protection to user endpoints—providing additional layers of control and visibility. […]
Closing the Loop on Silent Data Breach in Microsoft 365: How i-ARM Restores Visibility and Control

![]()
Microsoft 365 makes collaboration easy. With just a few clicks, users can share files and folders through links, streamlining teamwork across departments, partners, domains and even anyone. But that same convenience opens the door to link oversharing—especially when sensitive information is shared beyond what policy, security, or compliance standards allow. Link oversharing isn’t about how […]
Securing Data in the Age of AI: Outcomes of Implementing Microsoft Purview and the Infotechtion-ARM Solution to embrace and extend Purview
![]()
Data is the lifeblood of modern organizations—and one of the biggest targets for cybercriminals, insiders, and supply chain vulnerabilities. Sensitive information exists everywhere: in emails, collaboration platforms, cloud storage, legacy file shares, and increasingly in AI assistants like Microsoft Copilot. The challenge is not only knowing where sensitive data is, but also ensuring it is […]
The Operational Reality of Microsoft Purview

![]()
Microsoft Purview delivers powerful data governance capabilities, but operationalizing it across a large enterprise is often more complex than anticipated: (1) Inconsistent labeling across regions and business units, (2) limited reporting on policy enforcement and data classification and (3) difficulty in tracking operational issues (for example high false-positive rates) and responding to them in a […]

