What is Microsoft Priva?

![]()
So you heard us announcing the Microsoft Priva at our webinar – Establish an information protection and privacy strategy with Microsoft Principal Group Program Manager Nishan DeSilva. I will build on from the webinar and provide further insights into Microsoft Priva. Microsoft Priva is a new category of features in Microsoft Compliance Centre, providing solutions […]
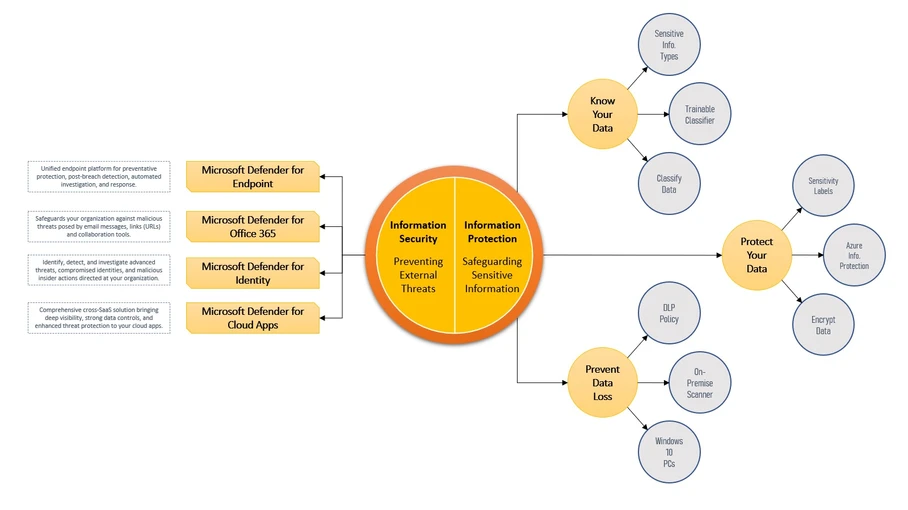
Microsoft Information Security vs Information Protection
![]()
Safeguard your Enterprise Information Ecosystem with Microsoft Information Security and Information Protection tools. Organizations nowadays have to be more resilient than ever. The need for organizations to remain Business As Usual (BAU) has increased exposure to external threats/risks by hackers, data theft, architectural loopholes, ultimately leading to customers’ lack of trust in the ability of […]
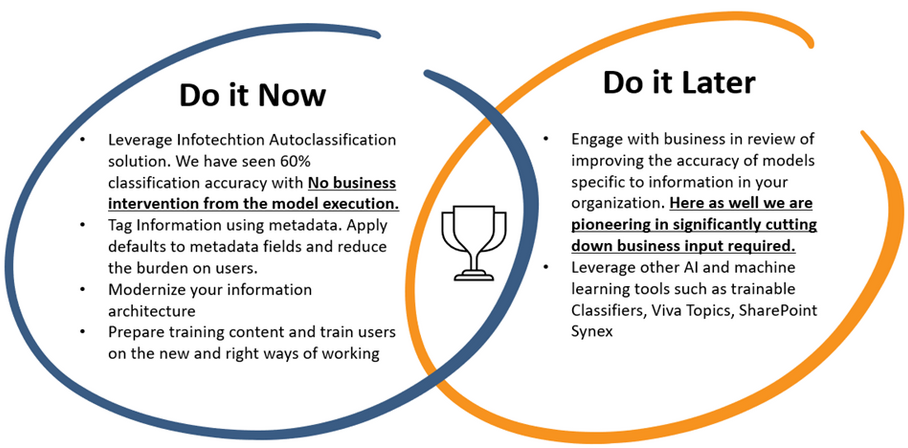
HOW CAN YOU AUTOMATE INFORMATION COMPLIANCE IN MICROSOFT365?
![]()
With the massive amount and a variety of data getting created at an accelerated growth, it has become crucial and difficult for organizations to govern, protect, and stay compliant. To avoid any kind of legal or security risk, it is important to detect and classify data accurately. It’s no longer possible for the users to […]
Relation hierarchy with hubs site (and Hub sites in Hub site)

![]()
We often talk about the importance of flat structure and using metadata to but contexts to content. Why would you use hub sites or even hub sites in a hub site? Let us first look at what hub sites are and what they can give you. We often use hub sites to create easier navigation […]
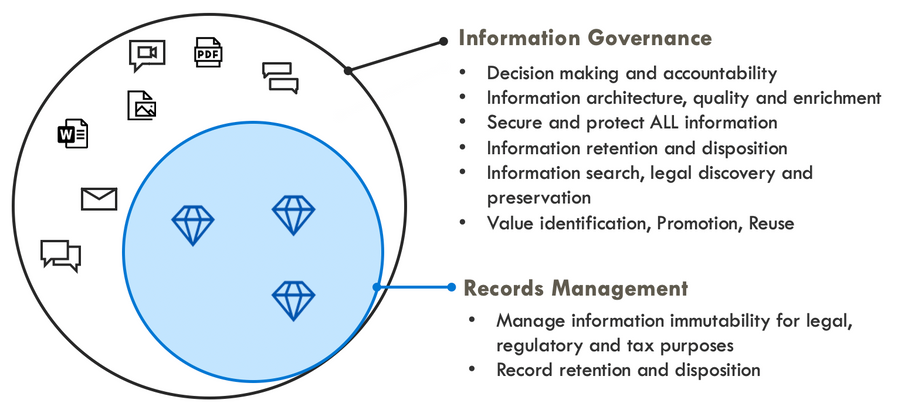
Best practices for Microsoft Records Management
![]()
Below are some of our resources addressing best practices for Microsoft Records Management. Establishing the business case Modernizing records management policies In-place vs centralised records management Big bucket retention categories Automate records management Metadata Taxonomies Lifecycle models Records declaration options Event-based retention Records revisions Adaptive policies Disposition reviews Multi-stage disposition reviews Access management Ensure compliance […]
M365 Information Protection Powers a Simple User Guide to Information Sharing

![]()
Microsoft365 integrated with Governance and Protection capabilities can significantly simplify many user experiences, specially when relates to sharing information internally and externally. Not only, you can better control which information is shared with external parties but also guide the users to ensure they make informed decisions. Infotechtion leverages multiple technology components – Sensitivity Labels, Auto […]
Information an Asset or a risk?

![]()
The rapid increase in digital collaboration provides challenges and opportunities for effectively managing Information, its reliability, retention, protection, and ability to find valuable information to support efficient business decisions. As work increasingly happens in Microsoft 365, governance (and its adoption) is an essential component of managing your corporate information and knowledge in the cloud. To […]
Webinar: Establish an information protection and privacy strategy for M365 and beyond

![]()
Automate how you discover, classify, and proactively protect sensitive information Tuesday January 18th, 2022 at 9am PT / 12pm ET / 18:00 CET Information and data protection, done well, presents a long-term opportunity to establish greater trust with customers and unlock employee collaboration and productivity, whilst minimizing security incidents, breaches and regulatory penalties. Most organizations […]
How can the process of selecting an outfit help us sort our documents?

![]()
If you ever had an important event approaching such as attending a wedding or a job interview, most of the times you would go through a selection of outfits and lay them in front of you. Once selection is made, you hang your outfit in front of you to have it ready to use on […]
10 steps to secure your M365 environment (part 2)

![]()
This is the second blog in a series about actions your organization can take to improve the security of your Microsoft365 tenant. You can find the first introductory blog here. The previous blog described the “Security Defaults” in Azure Active Directory (AAD) as a means to quickly implement MFA across your entire organisation. The ease […]

