5. Project Management Methodology – The PM Toolkit

![]()
Welcome back to The Project Management Toolkit series. So far, we’ve explored Employee Recognition, Collaborating with Clients, Onboarding a New Project Manager and Microsoft Project. This series breaks down the essential components of how Project Managers can take their leadership to the next level. Next, we’ll dive deep into a foundational decision every project manager […]
Building a Solid Legal Shield: Using e-Discovery to Protect Your Data

![]()
Building a Solid Legal Shield: Using e-Discovery to Protect Your Data What is e-Discovery? Many organizations overlook the full potential of Microsoft 365’s e-Discovery tools. These tools are crucial for identifying and managing electronic data required for legal cases or internal investigations, helping businesses stay compliant with legal and regulatory standards while enhancing data security […]
Investment and Benefit Strategy for Copilot

![]()
A strategic look at adding Copilot value Let me start with a quick segue into investments to provide a framework for maximizing your Copilot value. Many people invest in stocks by looking for the hottest opportunity. Investment funds by their nature are trying to bring together the top investments into a fund offering. It can be […]
M365 Implementations: Additional Insights on Change Management Challenges
![]()
A standard way of defining Change Management is “the management of change and development within a business or similar organization”, but what does that really mean for today’s Information Governance professionals? A common approach includes the following (easily found online and also used by most organizations): *Internal awareness materials, training information, defined feedback mechanism, predefined […]
Streamlining Compliance: Harnessing Entra ID Administrative Units within Microsoft Purview
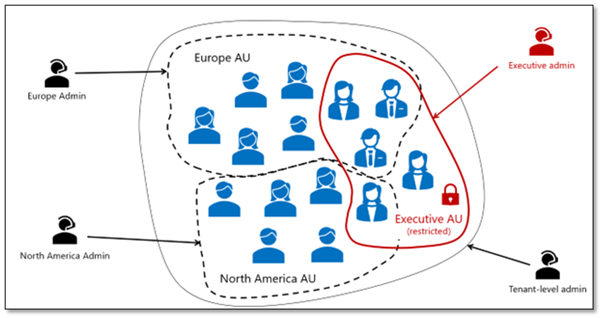
![]()
Administrators and Entra ID Administrative Unit (AU) Administrative Units are designed to provide organizations with a structured approach to managing directory objects, such as user accounts, by segmenting them into more manageable subdivisions. It is possible for user accounts to be simultaneously associated with multiple AUs. For instance, an individual’s user account might be included […]
Microsoft’s AI Offerings: From Copilot to Azure AI and Beyond

![]()
Within the last 50 years we had several technological booms that completely, and irreversibly changed our lives. Starting with the personal computer boom happening around 1980’s, then the Internet boom in the 1990s and 2000’s and Mobile Revolution in the 2000’s. For the past two years (as of writing this blog in 2024) we have […]
i-ARM Reporting Enabling Copilot Adoption and Risk Management

![]()
In today’s digital age, where technology rapidly evolves and integrates into every aspect of business operations, adopting advanced tools has become crucial. One such innovative tool is Copilot, designed to streamline various business processes through intelligent automation and data integration. However, with the adoption of such technology comes the need for robust monitoring and management […]
Discovery phase – what is it and why is it so important?

![]()
What is the discovery phase? Although it may seem obvious, many seem to be underestimating the importance of conducting a discovery phase before initiating a project. The discovery phase is often used as a pre-project, to gain an initial understanding of the situation as-is today. Creating a consensus of what the reality of the organization’s […]
So you learnt how to crawl, and now you want to run

![]()
So, You Think You are Ready to Run… But have you learned to walk yet?If you recall, in March we published a blog titled, “Fixing the Basics: The Importance of Learning to Crawl before Walking and Running,” in which we outlined some of the key foundational elements necessary to reach the goal of having an […]
Revolutionize Your Security: Dynamic Insider Risk Management with Adaptive Protection
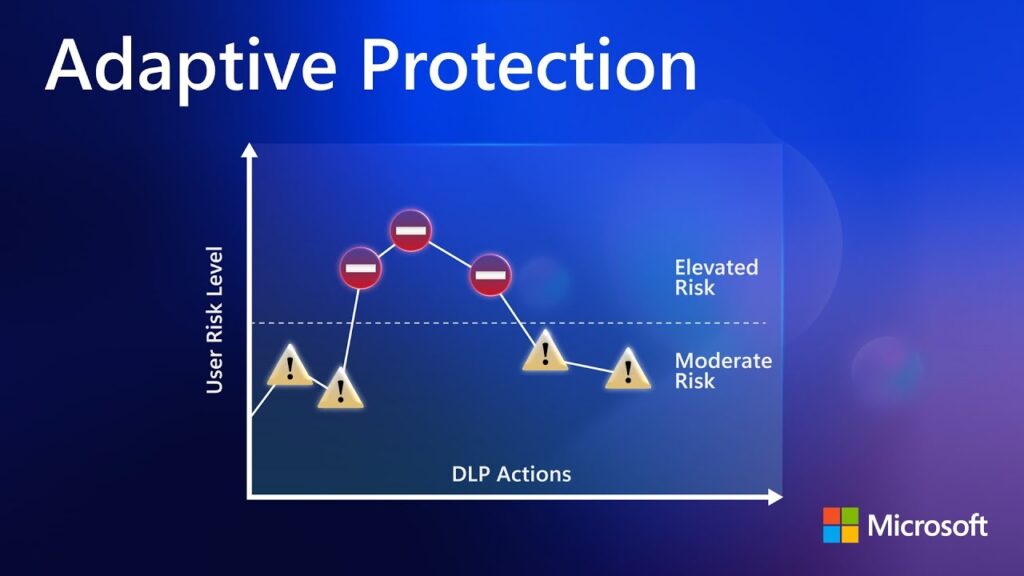
![]()
Since its inception in 2020, Microsoft Purview Insider Risk Management (IRM) has been the subject of extensive discourse and analysis. For those seeking a concise overview: IRM serves as an advanced analytical tool that synthesises diverse signals to pinpoint potential insider threats, whether they stem from intentional misconduct or inadvertent actions, encompassing intellectual property theft, […]

