![]()
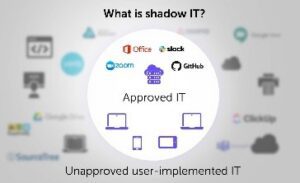
“Shadow IT is a term for SaaS applications employees access and use without the knowledge or permission of their information technology departments. Such applications aren’t inherently flawed or dangerous—“shadow IT” simply means an app is being used without IT’s explicit approval or oversight, which increases risk for an organization.”
Some typical shadow IT examples include:
· The Use of personal email accounts, such as Gmail, Yahoo, etc. for business communications
· Replicating existing software applications without adding new licences
· Use of unauthorized and unsanctioned hardware, like hard drives and portable storage devices such as a pen drive, CD, etc.
· Subscribing to third party SaaS applications such as video conferencing tools, desktop productivity tools, and various collaboration tools
· Personal Google drive components such as Google sheets or similar third party tools for storing company data, performing mail merge, etc.
· Use of free CRM tools to store customer information
Your users are in the cloud—even if you aren’t
Cyberattacks have become increasingly sophisticated in the ways they exploit the apps you have deployed in your on-premises and cloud infrastructures, establishing a starting point for privilege escalation, lateral movement, and exfiltration of your data. To understand the potential risks and stop these types of attacks, you need to gain clear visibility into your organization’s app compliance posture to quickly identify when an app exhibits anomalous behaviours and to respond when these behaviours present risks to your environment, data, and users.
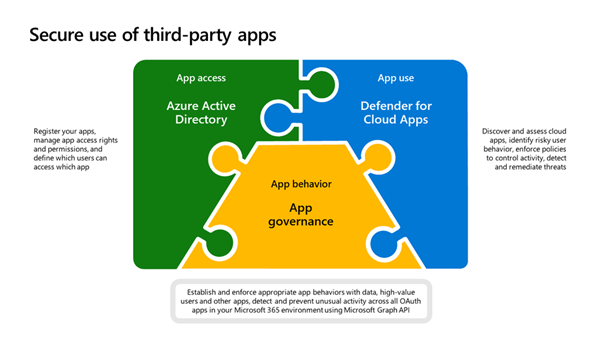
We recommend using the app governance add-on feature to Defender for Cloud Apps, which is a security and policy management capability designed for OAuth-enabled apps registered on Azure Active Directory (Azure AD). App governance delivers full visibility, remediation, and governance into how these apps and their users access, use, and share your sensitive data stored in Microsoft 365 through actionable insights and automated policy alerts and actions.
App governance provides you with comprehensive:
· Insights: See a view of all the third-party apps for the Microsoft 365 platform in your tenant on a single dashboard. You can see all the apps’ status and alert activities and react or respond to them.
· Governance: Create proactive or reactive policies for app and user patterns and behaviours and protect your users from using non-compliant or malicious apps and limiting the access of risky apps to your data.
· Detection: Be alerted and notified when there are anomalies in app activity and when non-compliant, malicious, or risky apps are used.
· Remediation: Along with automatic remediation capabilities, use remediation controls in a timely manner to respond to anomalous app activity detections.
App governance integration with Azure AD and Defender for Cloud Apps
App governance, Azure AD, and Defender for Cloud Apps collect and provide different data sets:
· App governance provides detailed information about an app’s activity at the API level
· Azure AD provides foundational app metadata and detailed information on sign-ins to apps
· Defender for Cloud Apps provides app risk information
By sharing information across app governance, Azure AD, and Defender for Cloud Apps, you can display aggregate information in one portal and easily link to another portal for more information.
Here are some examples
· App sign-in information in app governance:
o From the app governance portal, you can see the aggregated sign-in activity for each app and link back to the Azure Active Directory admin centre for the details of sign-in events.
· API usage information in the Defender for Cloud Apps portal:
o From the Defender for Cloud Apps portal, you can see API usage level and aggregate data transfer and link to the app governance portal for the details.
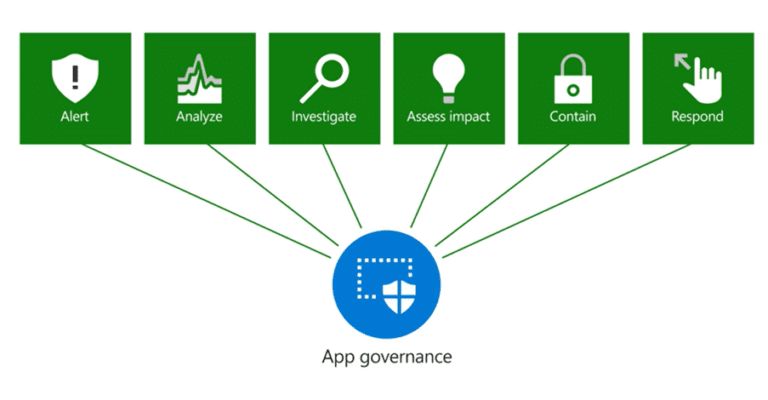
The integration of app governance with Azure AD and Defender for Cloud Apps
App governance sends its alerts to Microsoft 365 Defender to enable more detailed analysis of app-based security incidents. App governance alerts show up in Microsoft 365 Defender alerts list as alerts with the Detection source field set to “App Governance”
Does your company need some support to design and launch compliance initiatives? Contact us and talk to one of our experts or request a demo. We are excited to show you Infotechtion teamwork and information governance solutions!